What is Koronavilkku?
“Koronavilkku is a contact tracing app produced by the Finnish Institute for Health and Welfare (THL) to help you find out whether you may have been exposed to coronavirus. If you have a coronavirus test and are diagnosed as infected, you can use the app to share this anonymously with those you have been in close contact with.”
The application has been published as open source – to specifically facilitate independent evaluation of the application.
For more information on this, read the announcement.
The code is published on github:
- https://github.com/THLfi/koronavilkku-backend
- https://github.com/THLfi/koronavilkku-ios
- https://github.com/THLfi/koronavilkku-android
Why are we looking at this
At Mint Security we love context and context is very important here. The scan and the report is about code but also about process. Developing secure code and developing it securely is not just a one-off. For this reason, Mint Security and Veracode is open for scanning requests by the Koronavilkku development team in the future as well.
Conclusions
The application proved to be of very high quality securitywise. There were no significant security findings. We work with both customers and prospects with the Veracode SAST and SCA tools, and see many different applications and scanning results. The results here were above average – very much so.
Responsible disclosure
While the application is open sourced and thus available for anyone to analyze and poke around with (and have opinions), we still wanted to respect the team behind this. We did our first scan on September 4:th, and then immediately passed on the results to the Koronavilkku development team. The results – more details later in this post – were reviewed by the development team and fixed within a few days. The rescan of the application, again pulled from the public repository, proved this to be true. Well done.
If you have any findings or issues with Koronavilkku, please do contact the Koronavilkku development team first – and only then reach for Twitter.
Findings and details
All findings were reviewed and assessed by Putsi and Thomas from Mint Security before releasing the reports.
Scan 1 - September 4th
SAST
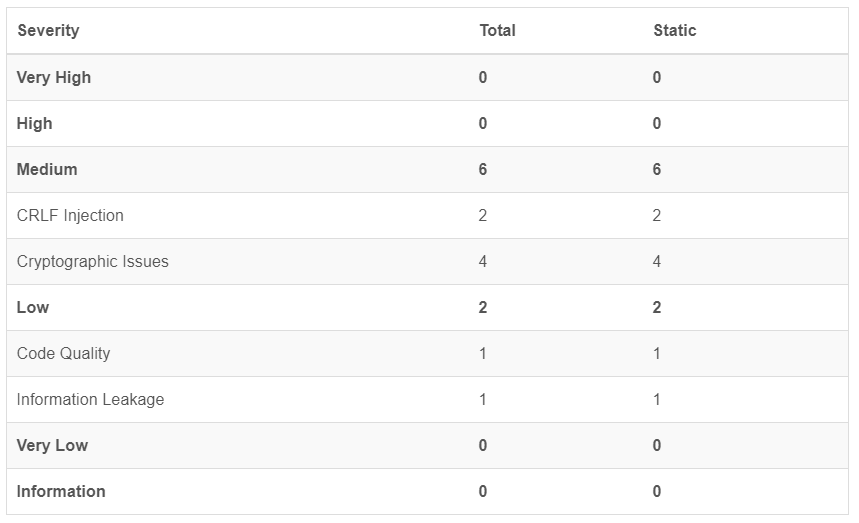
The scan revealed 6 medium and 2 low findings. None critical.
- Improper Output Neutralization for Logs – (some) exceptions were written as-is to the logs. By looking at the code, you can see that this is not a systemic error but rather a simple mistake.
- Insufficient Entropy – cryptograpic methods are used to generate id’s. The id’s are not used for any real cryptography, hence these are false positives.
- Cleartext Transmission of Sensitive Information – these findings are from debugging methods, hence no impact for the real application.
- Use of Wrong Operator in String Comparison – these findings are from debugging methods, hence no impact for the real application.
- Exposure of Sensitive Information Through Sent Data – these findings are from debugging methods, hence no impact for the real application.
SCA
No issues were found during SCA scan. Over 60 3rd party libraries are part of the analyzed Koronavilkku packages. This should be regarded as an excellent scanning result – well above average.
Scan 1 - September 16th
SAST
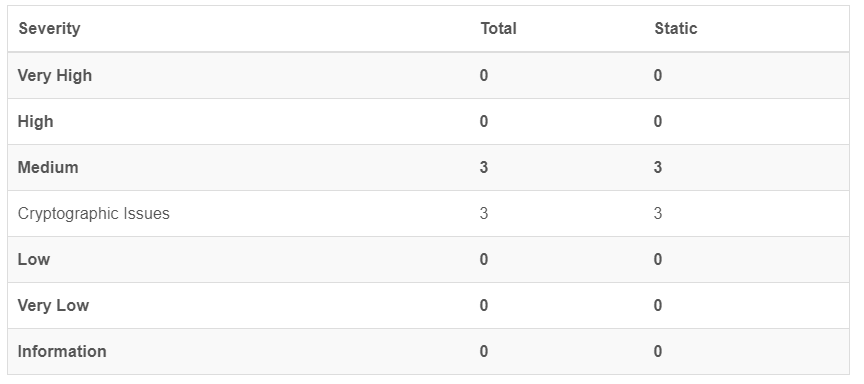
The scan revealed 3 medium findings. None critical. It is to be noted, that the Android package was not changed and thus not rescanned.
- Insufficient Entropy – cryptograpic methods are used to generate id’s. The id’s are not used for any real cryptography, hence these are false positives
SCA
One issue was found during SCA scan.
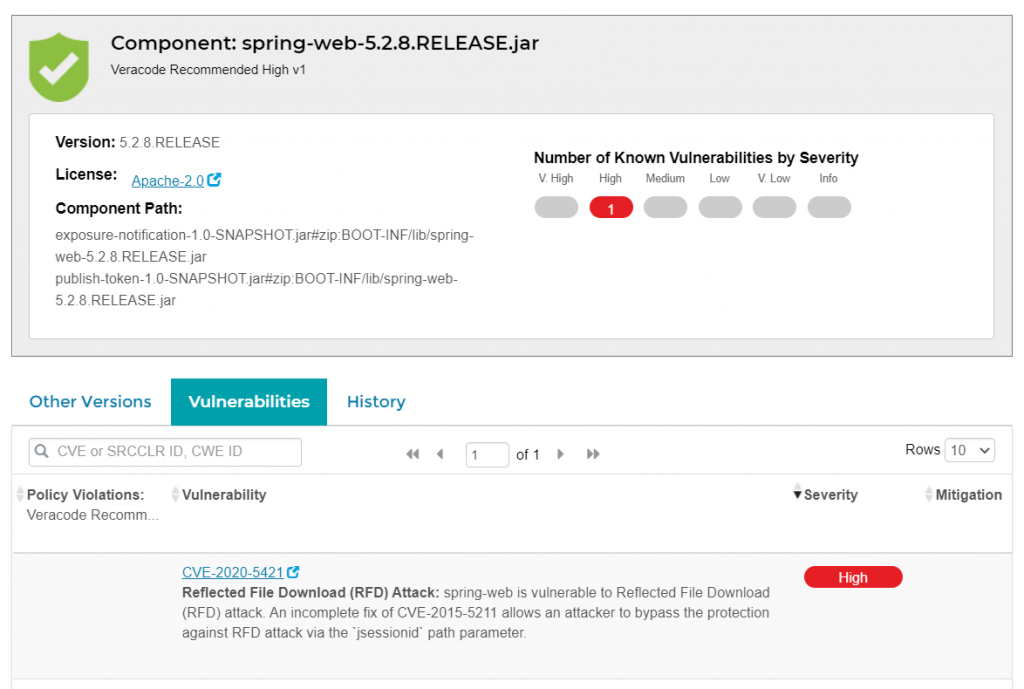
It is to be noted that managing 3rd party libraries is one of the most difficult tasks of modern software development. The Koronavilkku packages we analyzed have over 60 dependencies. It is also very important to understand that vulnerabilities in any of these 3rd libraries may be revealed and disclosed at any time, independently of the Koronavilkku developers and their software releases. This is the same situation as for all software making use of 3rd party libraries.
In this specific case, the version of the library included in Koronavilkku did not change between scans. It just so happens that between these scans, a vulnerability was found and flagged in this library and then shown in the SCA results of the later scan. Managing 3rd party libraries is a continuous and tedious process – overwhelming whithout proper tools and procedures.
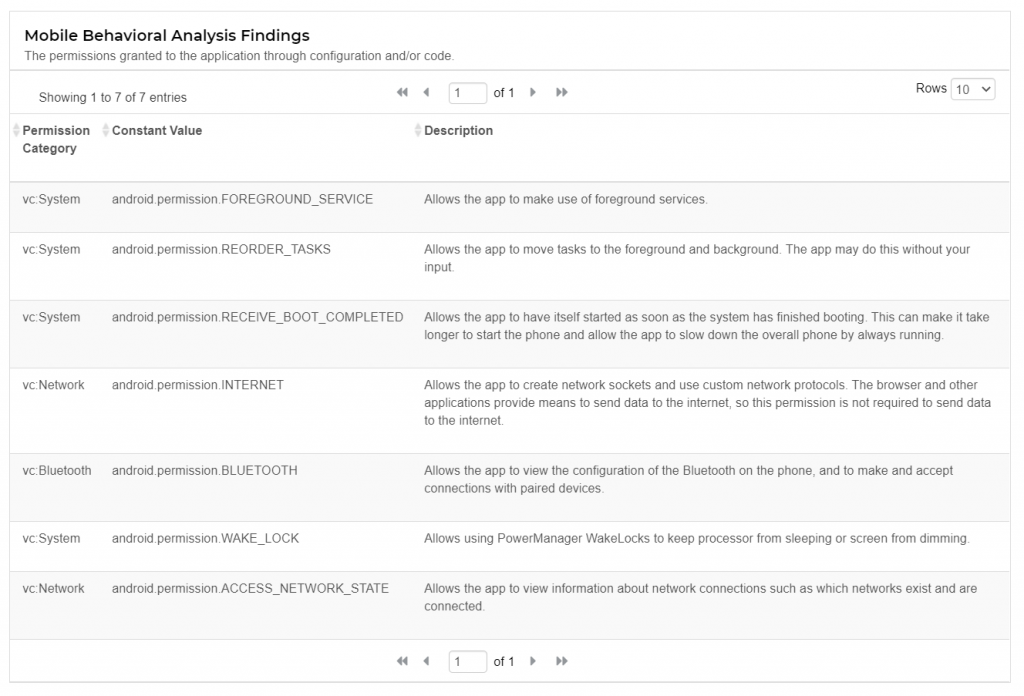
Mobile Behavioral Analysis
As part of the SAST scan, Veracode analyses and keeps track of permissions and other behavioral data points in the mobile device. This analysis is only related to the Android version of the application.
3rd party licenses
The 3rd party license report is here for pure readers interest only. Licenses are relevant in commercial development of applications but as Koronavilkku is open source software it is completely acceptable to use libraries with licenses not necessarily otherwise compatible with normal commercial software development,
-
HIGH IMPACT
- LGPL 3.0
- LGPL 2.1
- GPL 2.0 -
MEDIUM IMPACT
- CDDL 1.0
- EPL 1.0 -
LOW IMPACT
- Apache 2.0
- MIT
- CC-BY 3.0
- BSD-2 Clause
The reports

Secure Software Development Lifecycle
Secure Software Development Lifecycle Secure Software Development Lifecycle in Brief A secure application development process combines the coders’ instructions, security policy requirements, reports for the
Veracode
SAST – Static Application Security Testing SCA – Software Composition Analysis SDLC Integration Manage Your Entire Application Security Program on a Single Platform Veracode’s unified

Understanding your open source risk
As the use of open source code in development projects continues to grow exponentially, software development teams must take great pains to address open source risk.
Veracode Security Labs
Developers are, in effect, the only people in any organization who can fix vulnerabilities hidden in their applications. Veracode Security Labs helps meet the requirements of security standards while providing a meaningful way for the entire development team to learn more.








