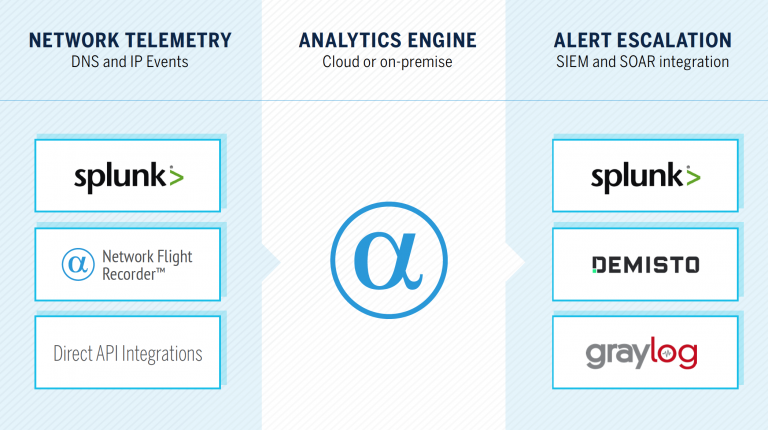
Through Network Behavior Analytics for Splunk and our native integrations for Demisto and Graylog, we instantly enrich network indicators (FQDNs, URLs, and IP addresses) to provide security teams with hunting material.
In this post, I describe some of the key classifiers within the AlphaSOC Analytics Engine, the public API we operate, and how teams consume our context data to uncover emerging threats that don’t have signatures.
Imposter Detection
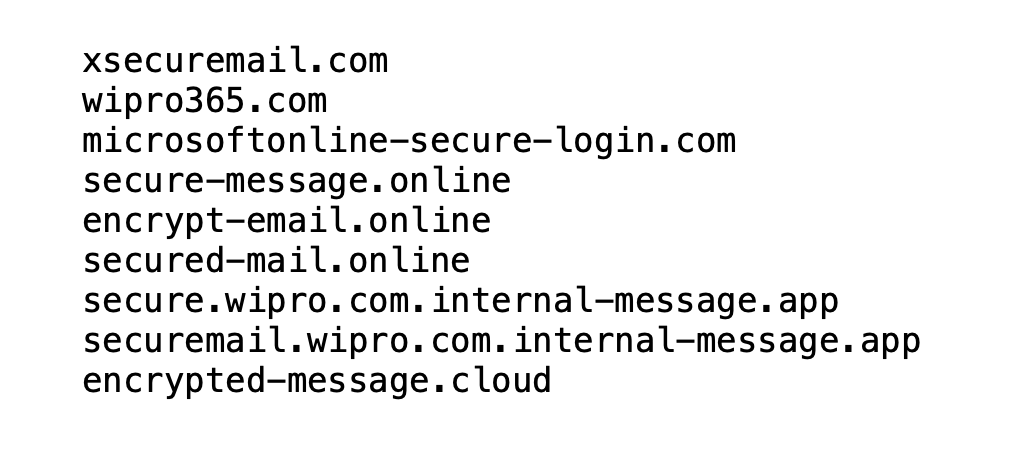
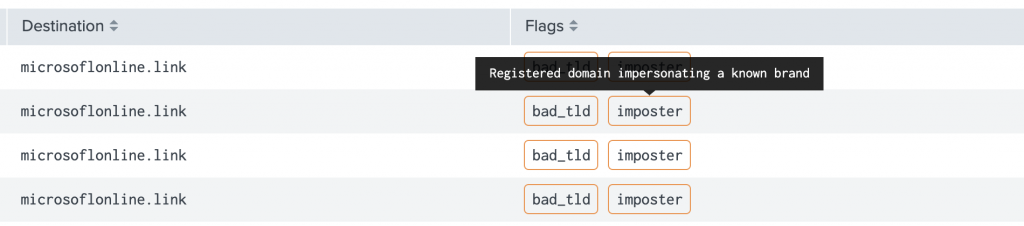

To drop any non-starters (e.g. user typos) the engine verifies that:
- The domain exists via DNS / WHOIS lookup
- The domain isn’t owned by the respective company (e.g. Dropbox)
- The infrastructure isn’t operated by a phishing simulation provider
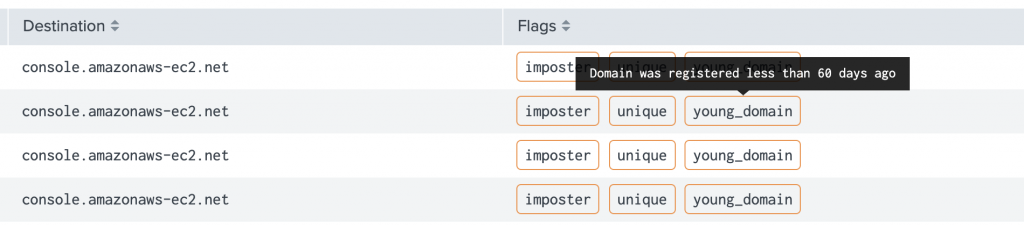
Highlighting Unique and Young Domains
Active Scoring and Fingerprinting
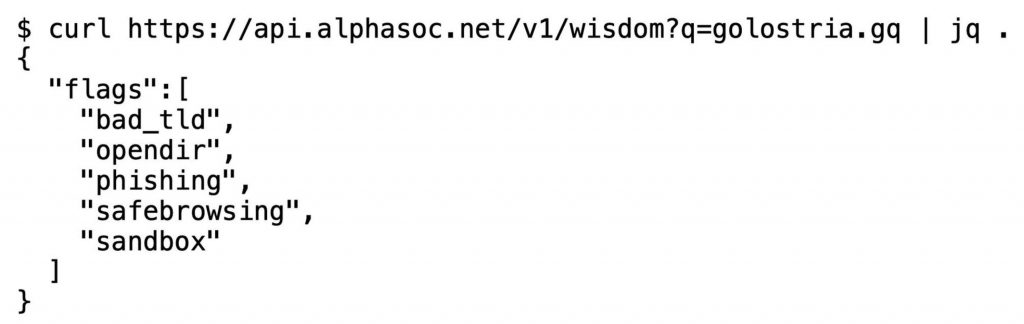
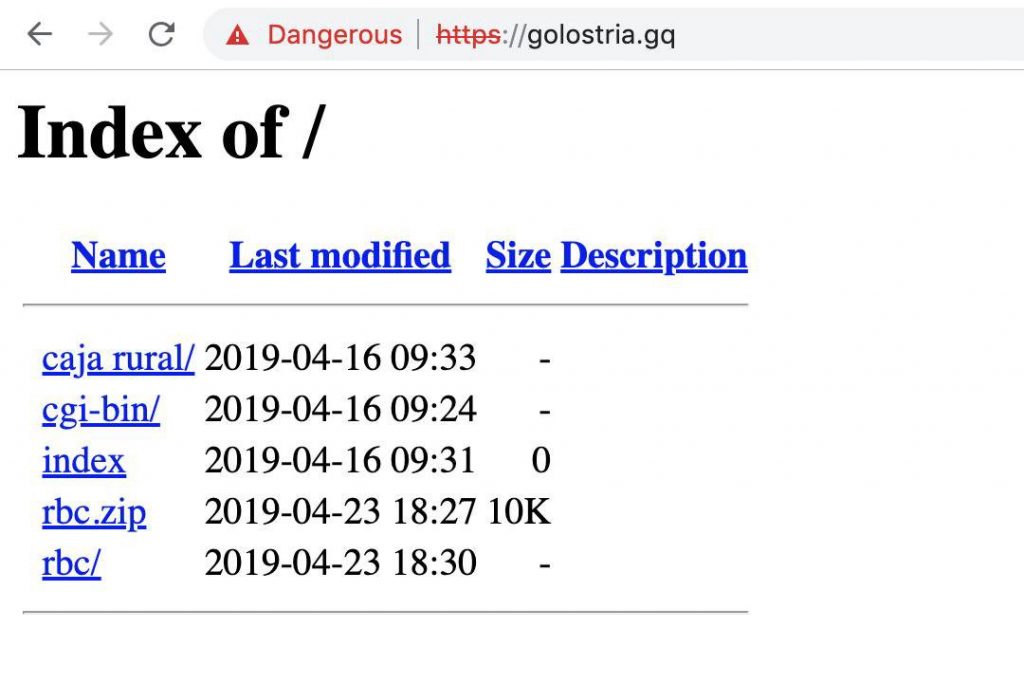
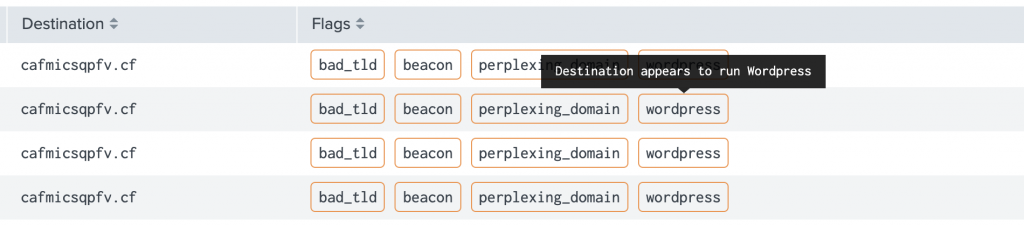
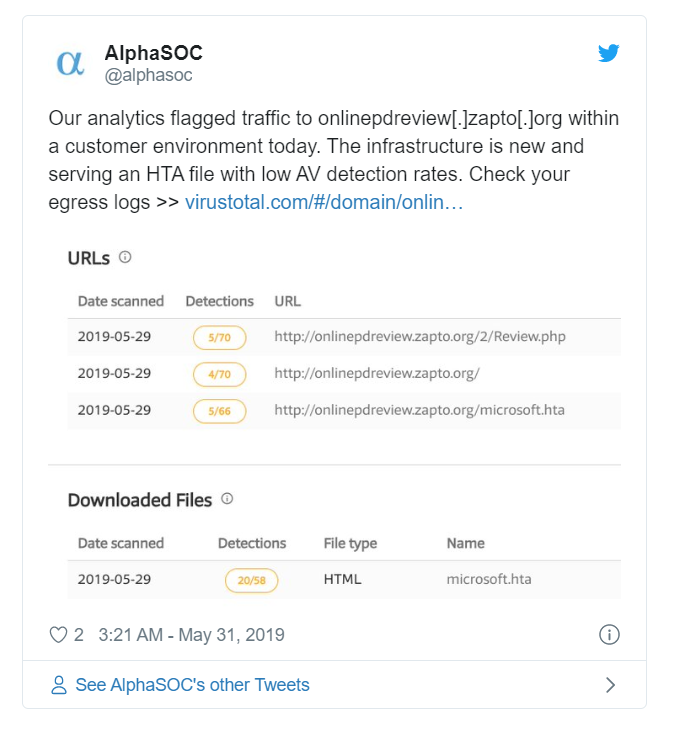
Uncovering Emerging Threats in Practice
AlphaSOC
Instantly identify infected hosts Uncover data exfiltration channels Threat hunt with high fidelity alerts Accurately identify security threats Hundreds of security teams around the world

Uncover Detection Blindspots with Network Flight Simulator
Today at AlphaSOC we released Network Flight Simulator (flightsim) 2.2.1, which is our free, open source adversary simulation tool. This latest release includes a number of new modules that security teams can use to instantly evaluate detection and response coverage within SIEM and SOAR tools.