Azure & M365 Security
Cyber, SecOps & Architectures
Azure & M365 Security in short
Azure and M365 security involves optimizing and strengthening Microsoft cloud security, including O365 services, to meet organizational needs. We consult clients on identity and access management, security policies, and best practices using Entra, Intune, Defender, and Purview. Our goal is to fine-tune Microsoft’s security mechanisms to effectively support business operations without unnecessary restrictions.
For us, supporting business operations means ensuring that both IT and leadership can confidently trust that users can perform their daily tasks securely with the provided tools, minimizing risks of security breaches and incidents. We also assist in security architecture design, helping organizations secure and manage their M365 and Azure environments, including workstations and mobile devices.
Our mission is to provide clients with a comprehensive understanding and best practices for operating securely within the Microsoft ecosystem.
What Mint Security delivers
We provide design, deployment, hardening, continuous monitoring, and optimization for Microsoft security solutions. Our standalone security assessments for Azure, M365, and O365 environments are available as part of our security testing services.
Our Key Services Include:
- Configuring baseline security settings for O365
- Hardening O365 environment configurations
- Secure Score-based, prioritized security actions
- Optimizing email and phishing protection settings
- Entra group design and user management assessments
- Deploying Intune for workstations and mobile devices
- Custom security hardening and configurations for endpoints & applications via Intune
- Customizing Microsoft baseline security configurations
- Hardening security settings for Office applications
- Implementing Microsoft Defender for threat protection
- Deploying Purview & Data Loss Prevention (DLP) policies
- Configuring Conditional Access rules
- Environment management & admin security best practices
- Deploying and optimizing Microsoft Sentinel (read more about it here)
- Optional: SOC-style continuous security monitoring and optimization via Sentinel
Our approach ensures that your Microsoft ecosystem is not only secure but also optimized for efficiency.
Customer needs and challenges to be solved
Enhancing an organization’s security posture within Azure, M365, and O365 is often too vast and complex to handle solely in-house. We help define the right strategy, identify critical security gaps, and ensure maturity progresses in a structured manner. Our consulting services bridge missing expertise, offering practical solutions to resource challenges, incident analysis, and outsourcing needs.
Common Challenges We Address:
- Overwhelming scope – Where to start and how to break it down
- Lack of specialized expertise and general resource constraints
- Achieving the right security maturity level within the required timeframe
- Incident assessment and analysis
- Evaluating outsourcing needs and defining a viable outsourcing strategy
- Current IT providers taking an overly IT-centric approach instead of a security-first focus
We ensure that your security investments are aligned with business priorities, balancing practicality, risk reduction, and operational efficiency.
More details about our methods and tools
We leverage our internal reference implementation as a foundation, which is not only extensively tested but also reviewed and validated by external experts. Our implementation is based on Microsoft’s best practices, supplemented with the most up-to-date information from various sources to ensure that our solutions continuously evolve with the ever-changing technology landscape.
We have strong experience in managing both Windows and macOS operating systems, and our expertise also covers the efficient management and security of iOS and Android mobile devices.
- Defender: Microsoft’s security suite providing threat protection, endpoint security, and advanced threat detection across devices, identities, and cloud environments.
- Purview: Microsoft’s data governance and compliance solution that helps organizations classify, protect, and manage sensitive information across their cloud and on-premises environments.
- Intune: A cloud-based endpoint management solution for securing and managing mobile devices, applications, and PCs across an organization.
- Azure: Microsoft’s cloud computing platform offering infrastructure, AI, and development services to build, deploy, and manage applications globally.
- O365: A collection of cloud-based productivity and collaboration tools, including Outlook, Word, Excel, and Teams, primarily focused on business efficiency.
- M365: A comprehensive subscription suite that includes Office 365, Windows 10/11, and enterprise security and compliance features for organizations.
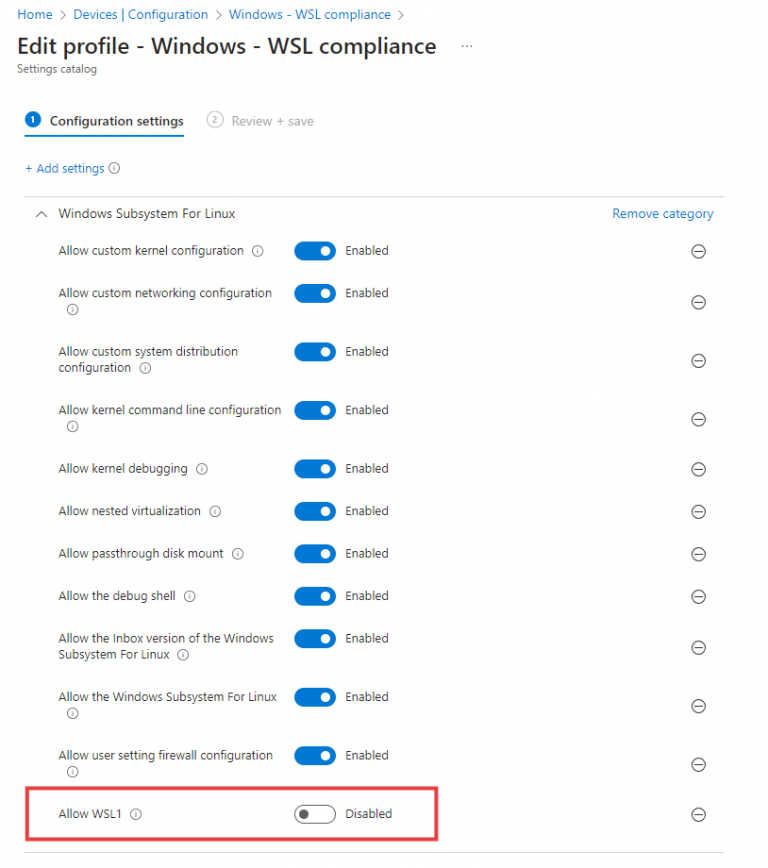
WSL – Defenderin sokea piste
Intune ja läjä policyja käytössä. Defender enrollattu joka Windows-koneelle. Defender huomaa mikäli käyttäjä ajelee vaarallisia asioita, eikö? Melkein.
Huom. tässä blogitekstissä oletetaan että Intune, Defender portaali ja WSL ovat lukijalle jollain tasolla tuttuja käsitteitä.)
