
- Cloud Governance
- Support for all major vendors
- Control your security posture
A force multiplier to the public cloud
Cloud environments are dynamic. Security should actively protect cloud workloads and services from modern attacks, enabling the cloud to stay agile and elastic. Dome9 simplifies public cloud security, allowing visualization and enforcement of the security posture consistently across public cloud services.
Dome9 visualizes and assesses the security posture, detects misconfigurations, models and actively enforces security best practices, and protects against identity theft and data loss in the cloud. It is a comprehensive software platform for public cloud security and compliance orchestration.
Full security visibility and control
Security capabilities currently cover Amazon Web Services, Microsoft Azure, and Google Cloud Platform (GCP). The service integrates natively through cloud providers’ API and provides cloud-agnostic policy orchestration on top of the native controls.
With Dome9, gold standard policies can be enforced across accounts, projects, regions and virtual networks and ensures the infrastructure conforms to regulatory compliance requirements and security best practices – at all times. Protection against identity theft is included by enforcing just-in-time privilege elevation for the most sensitive publc cloud operations.
- Cloud services and applications are never exposed
- Continuous compliance for cloud native services
- Auto-remediation of security misconfigurations
- Active protection against identity theft and data loss

of your AWS, Azure and Google Cloud
platforms at any scale

security misconfigurations in-place

against vulnerabilities and attacks
Visualize assets, assess security posture,
fix misconfigurations and threats,
manage the cloud firewall, and enforce security
from a single source of network authority.
CloudGuard Dome9 provides powerful visualization capabilities, giving intelligent visibility and situational awareness of the network security in your cloud environments
• Agentless, automated information gathering from public cloud environments
• Auto-classification of protected assets based on level of exposure to the outside world
• A real-time view of your network topology and workflow across network security groups (NSGs), VNets, subscriptions and regions
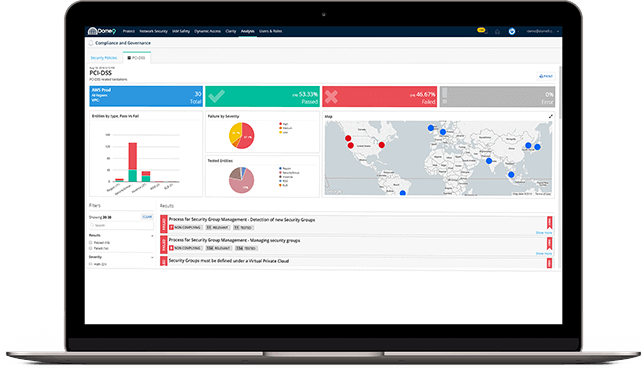
Manage the compliance lifecycle
for standards such as PCI DSS
— from automated data aggregation
and assessment to remediation and reporting.
The CloudGuard Dome9 Compliance Engine delivers continuous compliance and enforcement of governance and security best practices.
• Automated data aggregation for faster compliance audits and security assessments
• Built-in Best Practices bundle with over 200 security checks
• Continuous monitoring and alerting of non-compliance
Protect against compromised credentials
and identity theft using a cloud’s native IAM capabilities
to safeguard access to actions that can have a big impact.
The Tamper Protection capability of CloudGuard Dome9 allows you to lock down your security posture by preventing unauthorized configuration changes, enforcing a security gold standard at all times.
• Continuous monitoring of cloud accounts for changes outside the CloudGuard Dome9 system
• Automatic rollback to last known/approved state
• Independent third-party audit of unauthorized changes
Strengthen security even further
using a cloud-native security intelligence technology
that delivers cloud intrusion detection,
network traffic visualization and user activity analysis.
Dome9 allows visualization and analysis of network activity and traffic into and out of the cloud environment. With this, traffic from unwanted sources can be identified, or gaps in network security settings (which can then be fixed using other features of the Dome9 console).
Network flow logs can be analyzed to visualize the activity on the cloud network, and use queries to show traffic of interest. Dome9 has included many common queries and additional custom queries can be created with a graphical query builder based on the Dome9 Governance Specification Language (GSL).
Dome9 combines cloud inventory and configuration information with real-time monitoring data from a variety of sources including VPC Flow Logs, CloudTrail, AWS Inspector, as well as current threat intelligence feeds, IP reputation and geolocation databases. This results in enhanced visualization that highlights suspicious traffic from legitimate traffic. For example, sources of network traffic from other AWS elements are shown according to type, and malicious external sources are marked as such.
- near real-time view of events
- fine-tuned queries for specific events and threat hunting
- enriched contextual information from various log sources allows gain of
a quicker and clearer understanding of events that occur on the network
