- Network Scanning
- Web App Scanning
- Human Behaviour Scanning
 Holm Security Vulnerability Management Platform
Holm Security Vulnerability Management Platform
Protects your organisation by detecting vulnerabilities before any malicious person or organisation does. The platform includes vulnerability assessment for networks and websites, risk analyses for social engineering and a variety of tools that facilitate continuous safety work.
The platform helps you and your management to see how secure your IT environment and your users are against external threats such as hackers – whether you manage your own IT environment or outsource. You can manage the service easily and efficiently with our web-based Security Centre control panel. The platform is delivered from ultramodern and secure data centres
 The most efficient way to understand your security
The most efficient way to understand your security
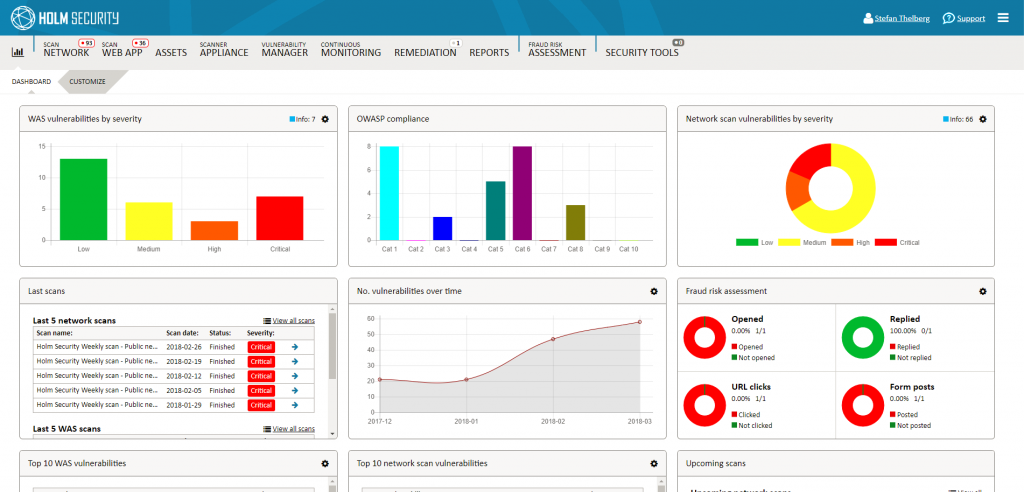
Take control of the security of your networks and systems with our network scanning. The service scans for more than 58,000 vulnerabilities. Irrespective of whether you manage all of your IT yourself or outsource, our network scanning is the most effective way to understand how secure you are against external threats, to rectify vulnerabilities and increase your cyber security requiring only a small investment in time. The service offers a range of GDPR and NIS compliance support functions.
Automated and continuous scanning of network and systems
Our network scanning automatically and continuously scans your networks and systems for an ever-increasing number of vulnerabilities. Network scanning detects vulnerabilities related to old software, exposed services and functions, misconfigured systems, weak passwords etc. In addition, the service automatically maps your network to give you a clear overview of all your systems – regardless of geographical location and whether you manage all your IT yourself or outsource all or part of your IT environment.
Using comprehensive information, smart and effective tools as well as our support and specialist help, you or your IT partner can effectively prioritise and rectify detected vulnerabilities before they are exploited by a malicious person.
In parallel with a scheduled scanning of your networks and systems, you can scan on demand at any time, for example in connection with changes and commissioning.
Covering the entire IT environment
Our cloud scanners scan your public networks and systems, accessible via the Internet. By installing one or more Scanner Appliances in your local environments, behind your firewalls, we can scan all your networks – even if your IT environment is present in several physical locations. All scanned data collected by our Scanner Appliances is presented in our cloud-based control panel Security Center.
Vulnerability manager
Vulnerability manager is a powerful tool for you to work effectively with vulnerabilities, regardless of whether you have a small number or thousands. You sort, group, ignore and prioritise the vulnerabilities in just the way that works best for you in the tool. The tool provides a range of functions for collaboration within your organisation and with external partners, such as your IT partner.
Continuous Monitoring
In Continuous Monitoring, you can quickly and easily set up monitoring of changes that generates notifications and alarms. This tool removes the need to work in Security Center. Instead, you will be notified when new vulnerabilities are detected, when any changes are made and when vulnerabilities have been rectified. You can easily pinpoint, for example, systems handling personal data for GDPR compliance or a specific network to obtain information about ports that are opened or closed.
Remediation
The service includes a complete tool for remediation. The flow is largely automated. You set up rules for when to create cases and how to assign them. The tool supports integration with external remediation systems.
Reports
A number of ready-made templates are available in the service, and you can create your own reports – adapted for both technicians and specialists, as well as management, CEO and the board. The reports are distributed in encrypted form to, for example, your IT partner or system vendor. In parallel to creating reports automatically according to your desired schedule, you can create reports on demand at any time.
Functions for GDPR and NIS compliance
The service offers a range of GDPR and NIS compliance support functions. You can, among other things, pinpoint your personal data systems to monitor these, and automatically generate continuous reports to the data controller.
 Web apps – a frequent attack vector
Web apps – a frequent attack vector
Several independent experts estimate that about 70% of all web applications (websites) can be hacked. Gartner states that 75% of the attacks occur in the application layer, which makes web applications the most vulnerable layer in your IT environment. The fact that web applications are often exposed to the entire Internet dramatically increases the risk of vulnerabilities being exploited by malicious people.
Automated and continuous scanning of web applications
Our web app scanning automatically and continuously scans your web apps and REST APIs for an ever-increasing number of vulnerabilities. Web applications detects vulnerabilities related to flawed code, misconfigured systems, weak passwords and exposed system information, personal data and code.
Using comprehensive information, smart and effective tools and our support service, you or your IT partner can effectively prioritise and rectify detected vulnerabilities before they are exploited by a malicious person.
In parallel with a scheduled scanning of your web applications, you can scan on demand at any time, for example in connection with changes and commissioning.
Covering the entire IT environment
Our cloud scanners scan your public web applications, accessible via the Internet. By installing one or more Scanner Appliances in your local environments, behind your firewalls, we can scan all your web applications – even if your IT environment is present in several physical locations. All scanned data collected by our Scanner Appliances is presented in our cloud-based control panel Security Center.
Vulnerability manager
Vulnerability manager is a powerful tool for you to work effectively with vulnerabilities, regardless of whether you have a small number or thousands. You sort, group, ignore and prioritise the vulnerabilities in just the way that works best for you in the tool. The tool provides a range of functions for collaboration within your organisation and with external partners, such as your IT partner.
Continuous Monitoring
In Continuous Monitoring, you can quickly and easily set up monitoring of changes that generates notifications and alarms. This tool removes the need to work in Security Center. Instead, you will be notified when new vulnerabilities are detected, when any changes are made and when vulnerabilities have been rectified. You can easily pinpoint, for example, web applications handling personal data for GDPR compliance.
Remediation
The service includes a complete tool for remediation. The flow is largely automated. You set up rules for when to create cases and how to assign them. The tool supports integration with external remediation systems.
Reports
A number of ready-made templates are available in the service, and you can create your own reports – adapted for both technicians and specialists, as well as management, CEO and the board. The reports are distributed in encrypted form to, for example, your IT partner or system vendor. In parallel to creating reports automatically according to your desired schedule, you can create reports on demand at any time.
Functions for GDPR and NIS compliance
The service offers a range of GDPR and NIS compliance support functions. You can, among other things, pinpoint your web apps that handle personal data to monitor these and automatically generate continuous reports to the data controller.
Send phishing emails and scan your users behaviour
Holm Security VMP contains an innovative and powerful tool to increase the resilience to social engineering. With this service, you simulate attacks by e-mail and, to increase resilience, customised training is automatically presented to each user based on the specific user’s behaviour. You will also get valuable statistics that provide the basis for further action.
The assessment is done without any risk to the user or your IT systems. The simulation uses e-mail messages and web pages. The service includes a variety of templates that you can easily edit, or you can create your own e-mail messages and web pages. In this way, you can carry out more or less advanced social engineering and so-called spear phishing attacks targeted at your entire organisation or a specific group of users within your organisation.
GDPR compliance
How prone are your users to leaking personal data? With the Fraud risk assessment service you can measure how resilient the users are to disclosing different types of personal data – an insight that is important in relation to GDPR.
Automated training
Depending on the behaviour of each user in the simulation, customised training is automatically composed and presented to the user. The information in the training is very useful for the user and is based on ready-made templates in the form of text and illustrations. The sender and the templates can be changed freely and it is possible to refer to your own training material. With a few clicks, automation helps you to not only get invaluable statistics, but also to automatically train your users – simple and very powerful.
Statistics
The results of the assessment consist of statistics of opened e-mails, clicks, e-mail replies and posted forms. The statistics are not connected to users, but are completely anonymised. You can easily compare the results from assessments at different times to evaluate whether the actions you have taken between the assessments have given the desired effect.
Privacy by Design
This service is based on the privacy by design principle, which means that the user’s personal integrity will never be compromised. All users are anonymous in the assessment and no sensitive data is stored.