MINT SECURITY PROUDLY PRESENTS
Überconsulting
Others make digitalization nice and usable.
We add trustworthy and secure.
Core Mint Services
Auditing & Security Testing
Identify and manage risk. Verify your security controls. Test your systems.
Administrative Security & Risk Management
Grow up. Formalize and show what you already might be doing correctly. Adhere to standards and regulation.
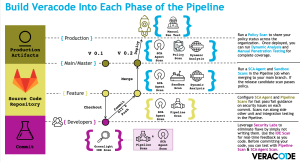
Software Development Security
Create better and more secure software. Find a security champion. Enable your team.
Cyber, SecOps & Architectures
The thrill of Cyber. Solutions for the technically minded. Secure Operations.
Need Security?
Contact our Professional Security Experts
sales@mintsecurity.fi
News & Blogs

Mint Security Oy has achieved ISO/IEC 27001:2022 certification
On December 9, 2024, Mint Security Oy achieved ISO/IEC 27001:2022 certification. With this certification, we want to show that we take the trust our customers

Network Management Best Practices: Optimizing Performance And Security
In the digital age, businesses rely heavily on their networks to function efficiently. However, managing and maintaining a complex network can be a daunting task. By implementing effective network management best practices, organizations can ensure optimal performance, enhance security, and minimize downtime.

Leveraging NetFlow For Network Security And Threat Detection
In the ever-evolving landscape of cybersecurity, staying ahead of sophisticated threats demands innovative solutions. One such game-changer is NetFlow, a technology that unlocks a treasure trove of network traffic data. By leveraging NetFlow, organizations gain the upper hand in safeguarding their networks and detecting potential threats.

Splunk vulnerability analysis – CVE-2024-29946 & CVE-2024-29945
Splunk vulnerability analysis – CVE-2024-29946 & CVE-2024-29945 in relation to a common threat model. DISCLAIMER – The author of this blog shall not be held responsible for any negative outcomes that may occur as a result of following advice given in this blog. Caveat emptor – use advice and ideas presented in this blog at your own risk.
Leverage our Frontline Expertise
Expertise isn’t born, it’s earned on the front lines.
We walk the walk.