Log Management & SIEM – Splunk and Sentinel
Cyber, SecOps & Architectures
Log Management & SIEM – Splunk and Sentinel
Situational picture is one of the biggest “hype words” at the moment. Most simply, situational picture is an overview into your cyber security posture, generated from several log sources. At its best, a situational picture includes application logs, data communication logs, customer feedback systems, ticketing systems, as well as public news sources, threat intel and possibly much more. Building all this is challenging; mapping and defining needs, and deciding what’s “good enough” is a cumbersome process.
What Mint Security delivers
We provide services in the following areas:
- Log management requirements analysis and planning
- Customer-focused SOC tenders and outsourcing
- SOC-driven SOC technology tenders
- Establishing in-house SOCs
- Splunk technology implementations and deployments
- Sentinel deployments
- Splunk and Sentinel integrations
- Creating a comprehensive security situational overview
We assist in identifying initial needs and can handle installations even in complex and challenging environments. We design log management architecture from the perspectives of performance, redundancy, log security, and overall cybersecurity. Controlling access to logs is a critical aspect of security.
Our expertise in audit logs is built on experience with highly demanding financial sector environments, and our skills scale accordingly.
We are technology-agnostic, but we excel in Splunk and Sentinel environments when it comes to technical implementations. However, in competitive bidding, we remain open-minded about different technologies.
Customer Needs and Challenges to Be Solved
Every customer environment is unique, and each client has specific needs. However, the challenges we address can generally be categorized as follows:
- Endpoint visibility
- Monitoring and alerting
- Compliance management
- Security device visibility
- Infrastructure visibility
- SecDevOps environment monitoring
- Runtime logging for system software
- Compliance and audit logging
- Application development environment and software security assessment
Sentinel
Sentinel plays a crucial role in a well-managed Microsoft 365 environment. It provides a streamlined way to monitor and track activity across Entra, Defender, Purview, Intune, and the entire Azure infrastructure. However, careful planning and budgeting are essential before implementation.
Once deployed, it’s equally important to establish clear processes for who is responsible for what and when.
With thorough preparation, an organization retains control over its most valuable asset—security monitoring—while having the option to outsource the more routine tasks, such as overnight monitoring, if needed.
Splunk
Already using Splunk!
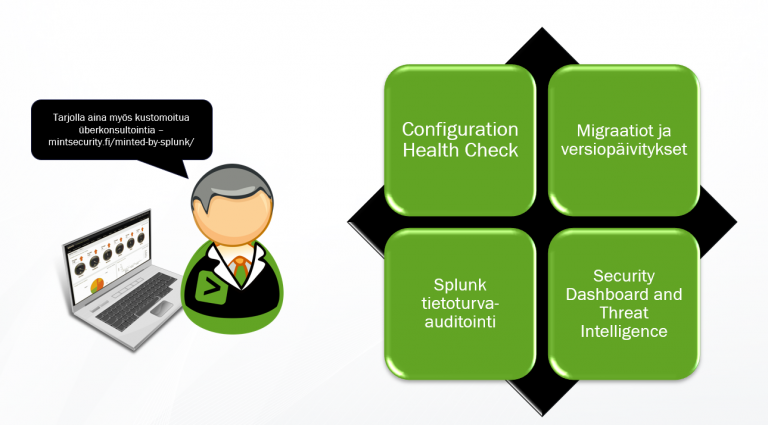
Mint Splunk Consulting Services
Mint Security tarjoaa Splunkia käyttäville erilaisia lisäarvollisia Splunk konsultointipalveluita jolla saadaan omasta ympäristöstä kaikki irti – turvallisesti.
We are looking to implement Splunk
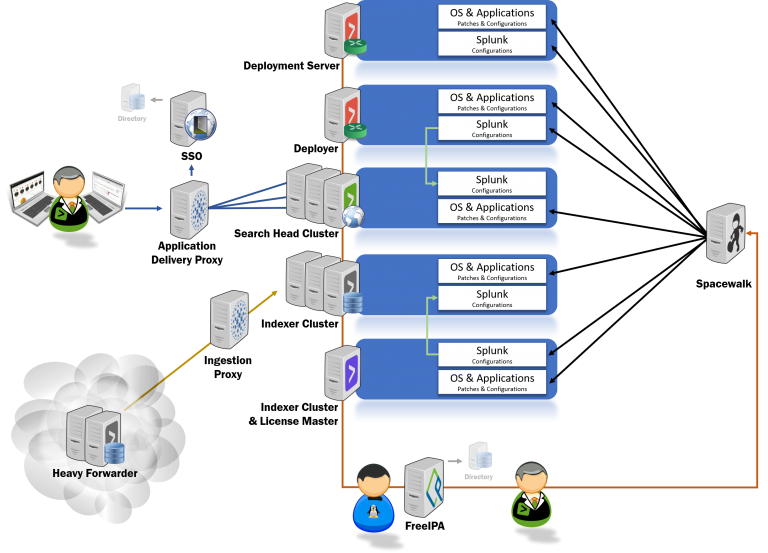
Splunk delivery models
Mint Security has a set of predefined delivery models to choose from. These are based on best practices and experience.
There is a lot to write about Splunk and the endless opportunities therein – so we have decided to share both expertise as well as opinions as separate blogs.

Installing Splunk with Ansible
Managing a Splunk installation can be a complex task, but with proper tools and processes, it will become a lot more approachable. Recently, a customer wanted to have a Splunk environment that they could install and manage with Ansible. So that is what we created.
Scaling and managing Splunk Enterprise Installation
Clustered Splunk Enterprise installations are mainly managed by the related management nodes. Indexer Cluster with the Cluster Master and Search Head Cluster with the Search Head Cluster Deployer. Without an additional process of change management, there is no way to easily track down what has been changed, by who and when.
More details about our methods and tools
We are hard-core Splunk experts. We have successfully brought our experience from over the years to Sentinel. Our expertise is not product-specific, but relying on our experience, we can conjure up views in big log data in any environment.
Below are some screenshots of actual (and anonymized) log analysis.

We do Splunk implementations worldwide. We prefer to do preparations offsite, initial planning as a workshop onsite, then installations and configurations over remote connections and finalization, training and handover again onsite. We have a clear concept, the final implementation is always up to the customer.

Splunk is one of the most popular and largest log management vendors today. Spunk is widely used, there are lots of extensions and addons even for the most exotic use cases. Splunk can go beyond huge amounts of data and does not limit the source types or log formats in any way. Whatever you throw at it, we will work it out without expensive and time consuming efforts.
As part of our commitment to delivering an end to end solution, we also provide licenses for Splunk.
