OWASP ASVS L2 assessment
Auditing & IT-Risk Management
OWASP ASVS L2 assessment in brief
OWASP ASVS is an information security framework used in software development and testing. ASVS level 2 is designed for applications that require a higher level of trust. This level is particularly relevant for applications that handle sensitive information — for example personally identifiable information, information about a company’s financial position, or other information that, if disclosed to third parties, could compromise privacy or otherwise harm the business.
ASVS level 2 goes beyond the basic security controls and can include both automated and manual checks.
What Mint Security delivers
Our assessment process is based on our diverse experience in software security projects and our experts’ knowledge of the ASVS standard. The goal of the entire process is to provide a detailed and accurate assessment of how well the application meets the strict security requirements of OWASP ASVS Level 2, identifying strengths and areas for improvement.
Key steps in the process outlined
- Preparation — we go through the essential aspects of the target application’s environment, utilized technologies and set safety goals with the customer.
- Execution — we conduct interviews and review the submitted documentation against ASVS level 2 requirements
- Reporting — we document our findings, including identified vulnerabilities, and make recommendations to fix identified issues as needed.
More details about our methods and tools
The ASVS assessment begins by getting to know the entity to be reviewed together with the customer. Based on this, decisions are made on the scope, limitations and other boundary conditions of the assessment.
It is important to agree on contact persons and/or contact points for the duration of the assessment. The right people or contact points are defined and documented by both Mint Security and the customer.
We will arrange suitable times for interviews and send appropriate calendar invitations.
We review the documentation and other similar information provided to us, determining the links to the ASVS requirements. This helps us to get a comprehensive understanding of the current security situation of the application.
Next, we conduct interviews with the right stakeholders and gather relevant information to understand the OWASP ASVS level 2 context. In addition, we analyze user documentation and system requirements to determine the degree of compliance with OWASP ASVS level 2 requirements and identify critical areas for risk mitigation.
If we identify deficiencies in the documentation or require further clarification of certain controls or security practices, we will request more detailed documentation or other additional information. This ensures that our assessment is thorough and takes into account all aspects of application security — just as required by OWASP ASVS level 2.
After the evaluation and interviews, we produce the final report and discuss its content with the client. If the discussion indicates a need for changes or clear errors are detected, we will correct the information.
Customer needs and challenges to be solved
By choosing our OWASP ASVS level 2 assessment service, we help ensure the security status of our customer’s application through a comprehensive assessment and in accordance with an internationally recognized framework. It is suitable for organizations that want to increase confidence in their application security or generally improve their security practices.
By conducting this assessment, companies can proactively address security issues, reduce the risk of data breaches, and build trust among their own customers and stakeholders regarding the security of their applications.
More details about our methods and tools
The assessment is carried out in one or more interviews covering predefined areas. For individual ASVS level 2 observations, we record its status (passed/failed/out of scope) and, if necessary, our free-form notes.
Our tools and methods include, for example:
- Comprehensive information security assurance — Our ASVS level 2 assessment includes a wide range of checks covering various aspects of application security, such as authentication, session management, access control, data validation, and API security.
- Source code assessment — depending on the situation, we may assess the source code of the targeted application.
- Documentation review — we review application architecture, dataflow diagrams, and other relevant documents to understand security principles.
- Risk-based approach — assessment is not only about identifying vulnerabilities, but also about understanding the risk context of the application. This includes the type of data being processed, its users and exposure to potential threats.
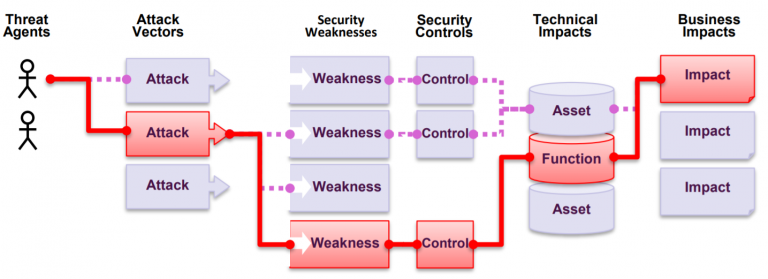
What is pentesting?
A common tool used to assess the security of a web application is penetration testing. Known also as pentest. Pentest is a “legal” simulated attack that seeks to use an application in a way that could be harmful to either the system, the data in the system, or the people who use the system.
