SIEM, Splunk & Log Management
Cyber, SecOps & Architectures
SIEM & Log Management in Brief
Situational picture is one of the biggest “hype words” at the moment. Most simply, situational picture is an overview into your cyber security posture, generated from several log sources. At its best, a situational picture includes application logs, data communication logs, customer feedback systems, ticketing systems, as well as public news sources, threat intel and possibly much more. Building all this is challenging; mapping and defining needs, and deciding what’s “good enough” is a cumbersome process.
What Mint Security delivers
We help identify the initial needs. We design the log management architecture from the point of view of performance, redundancy, log protection, as well as security. With regard to the protection of logs, it is essential who has access to which log.
In audit logs, our expertise is based on the demanding environments in the financial sector – our expertise is scalable both upwards and downwards.
Customer Needs and Challenges to Be Solved
Every customer environment is different and each customer has individual needs. However, the challenges we face can be roughly categorized as follows:
- Situational picture of security devices
- Situational picture of the infrastructure
- Situational picture of the SecDevOps environment
- Run-time logs for systems software
- Compliance and audit logs
- Visibility inbto SDLC, CI/CD pipelines and application development
- Visibility into the cloud infrastructure
- Integrating log observations in JIRA or Slack
Splunk
We have excellent expertise in Splunk. We prefer to do our SIEM deliveries with Splunk, because we can guarantee excellent results, we can support our customers all the way – planning, sizing, implementing, operating the system, managing content and creating alerts or SOC integrations.
Already using Splunk!
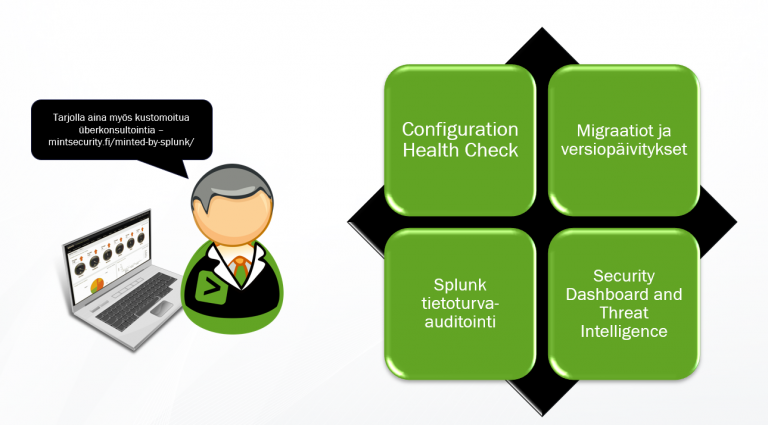
Mint Splunk Consulting Services
Mint Security tarjoaa Splunkia käyttäville erilaisia lisäarvollisia Splunk konsultointipalveluita jolla saadaan omasta ympäristöstä kaikki irti – turvallisesti.
We are looking to implement Splunk
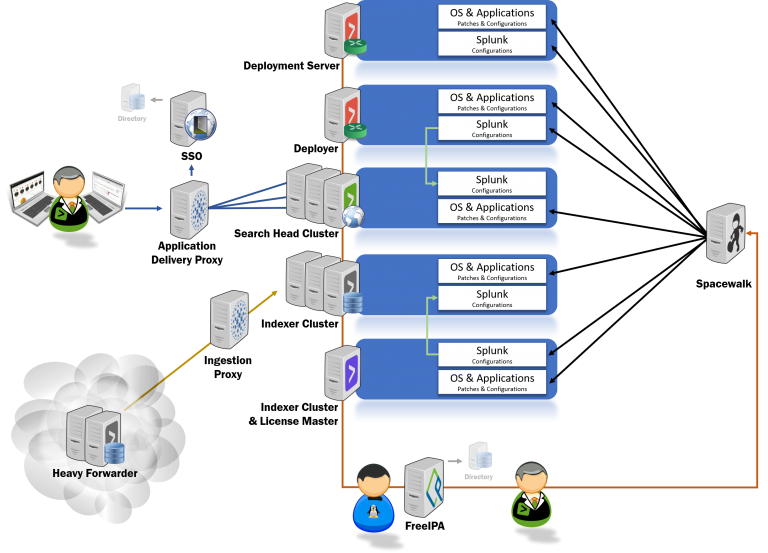
Splunk delivery models
Mint Security has a set of predefined delivery models to choose from. These are based on best practices and experience.
Our Excellent Splunk Blogs
There is a lot to write about Splunk and the endless opportunities therein – so we have decided to share both expertise as well as opinions as separate blogs.
Minted by Splunk
Mint Security is a Splunk partner and a license reseller. In addition, Mint Security provides a vast range of überconsulting for Splunk. From a single server to clustered multisite setups with integrated SSO and 2FA.
Getting started with Splunk Enterprise
Splunk Enterprise is known as a de-facto do-it-all log collector, that in reality is fairly easy to start with, but can be complex to master.
More details about our methods and tools
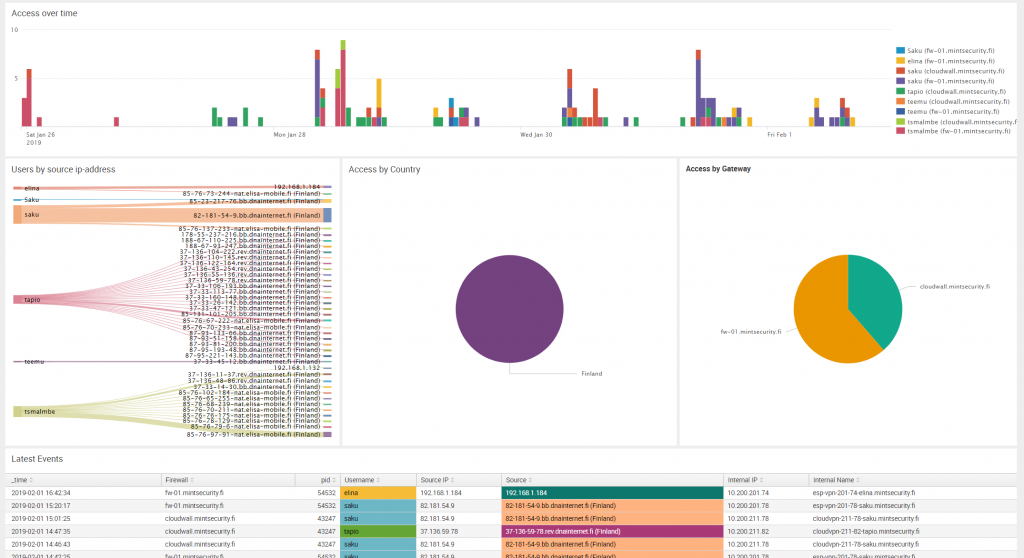
We are hard-core Splunk experts. However, our expertise is not product-specific, but relying on our experience, we can conjure up views in big log data in any environment.
Below are some screenshots of actual (and anonymized) log analysis.

We do Splunk implementations worldwide. We prefer to do preparations offsite, initial planning as a workshop onsite, then installations and configurations over remote connections and finalization, training and handover again onsite. We have a clear concept, the final implementation is always up to the customer.

Splunk is one of the most popular and largest log management vendors today. Spunk is widely used, there are lots of extensions and addons even for the most exotic use cases. Splunk can go beyond huge amounts of data and does not limit the source types or log formats in any way. Whatever you throw at it, we will work it out without expensive and time consuming efforts.
As part of our commitment to delivering an end to end solution, we also provide licenses for Splunk.
