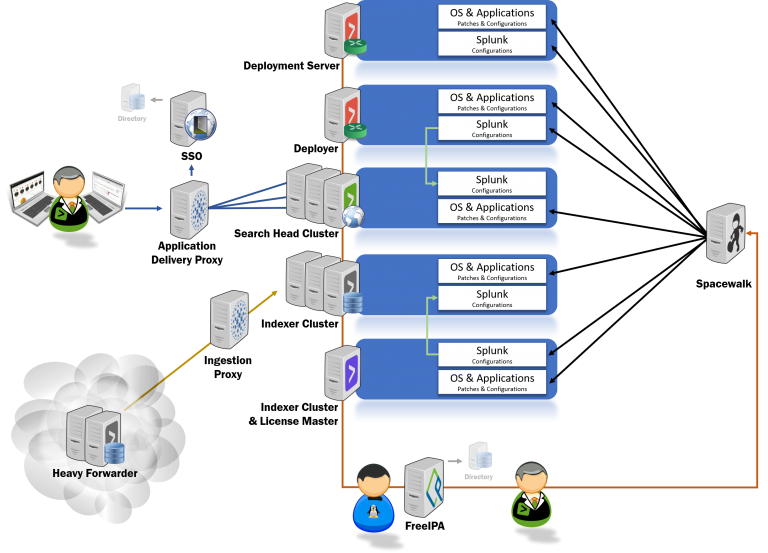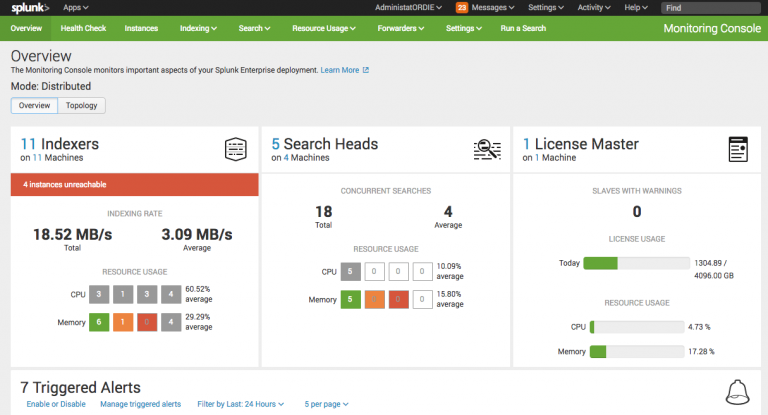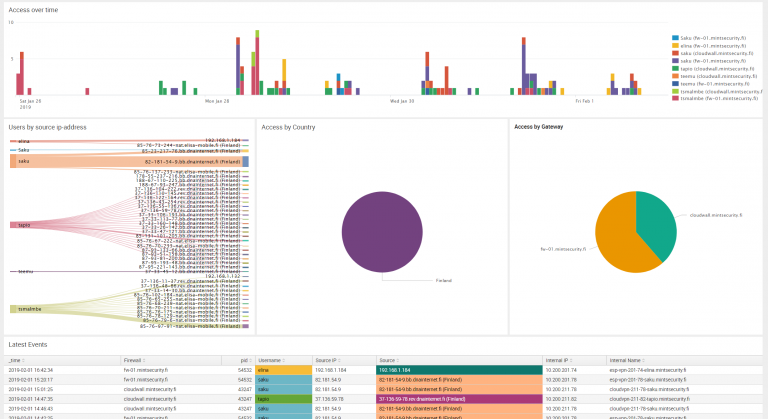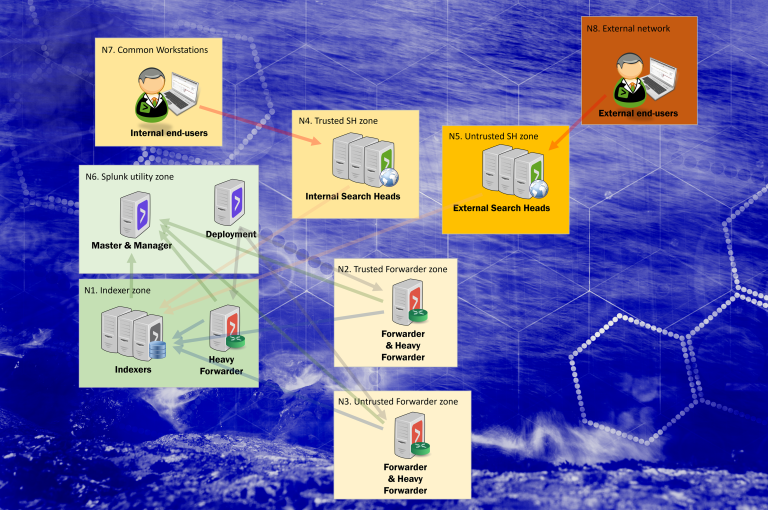
Trust boundaries and threat actors within the Splunk Enterprise ecosystem
Splunk Enterprise (on-premises) can be setup in a vast number of ways, including hardening through network segregation. Splunk components chosen in the diagram are there to highlight where and why trust boundaries may or should be implemented.