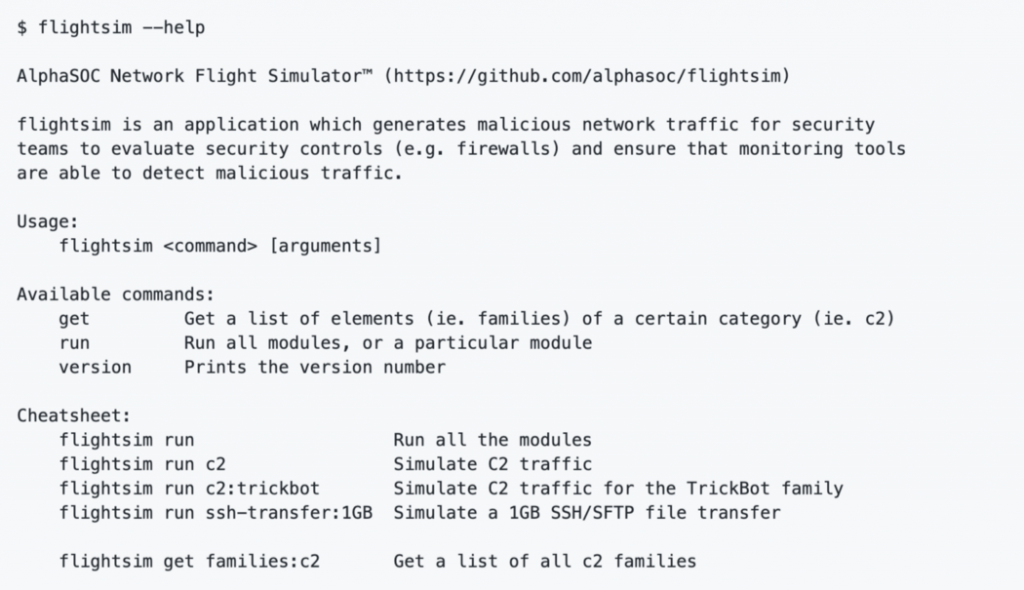
Installing Network Flight Simulator
The flightsim binaries are freely available for Apple macOS, Linux, FreeBSD, and Microsoft Windows, as found under the project’s releases page.
Network Flight Simulator is a command line tool that generates egress network traffic patterns from your system out to the public Internet. The idea is to safely synthesize malicious traffic patterns within your environment, so that you can check the configuration and coverage of your detection tools.
Upon unpacking, as below, you can execute flightsim run to invoke all of the modules and generate many different malicious traffic patterns, including C2 beacons, DGA events, cryptomining traffic, tunneling over DNS and ICMP, SFTP data exfiltration, and traffic to known malware sinkholes.
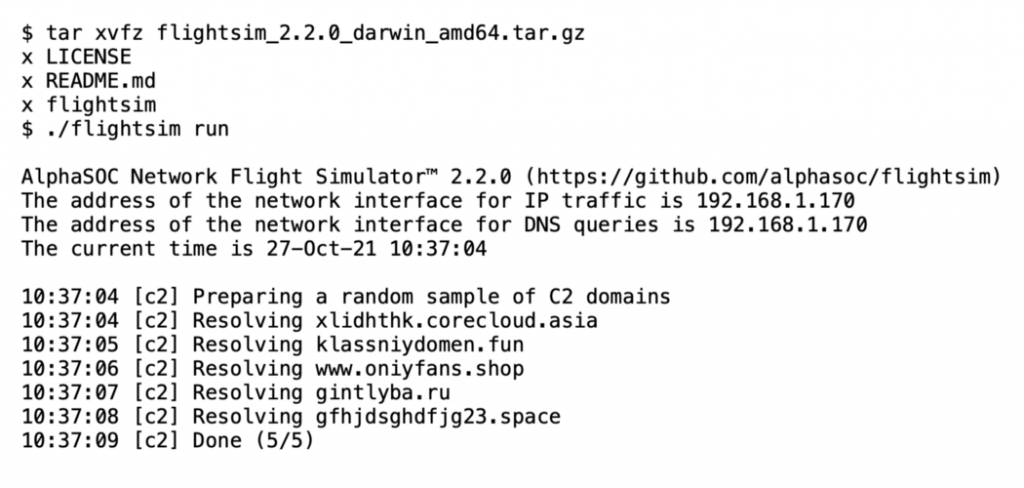
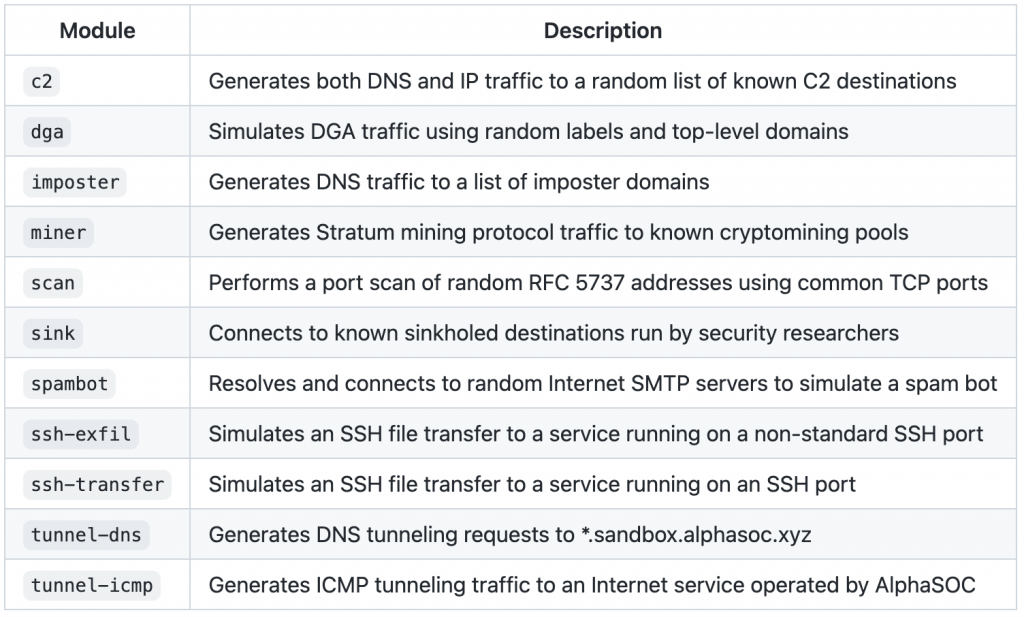
Simulator Module Breakdown
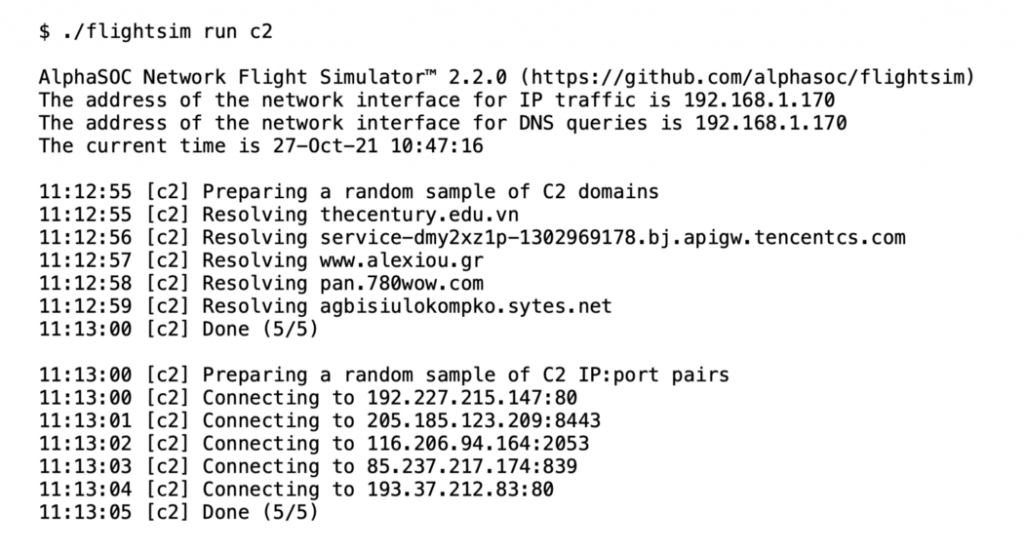
Simulating Command and Control (C2) Beacons
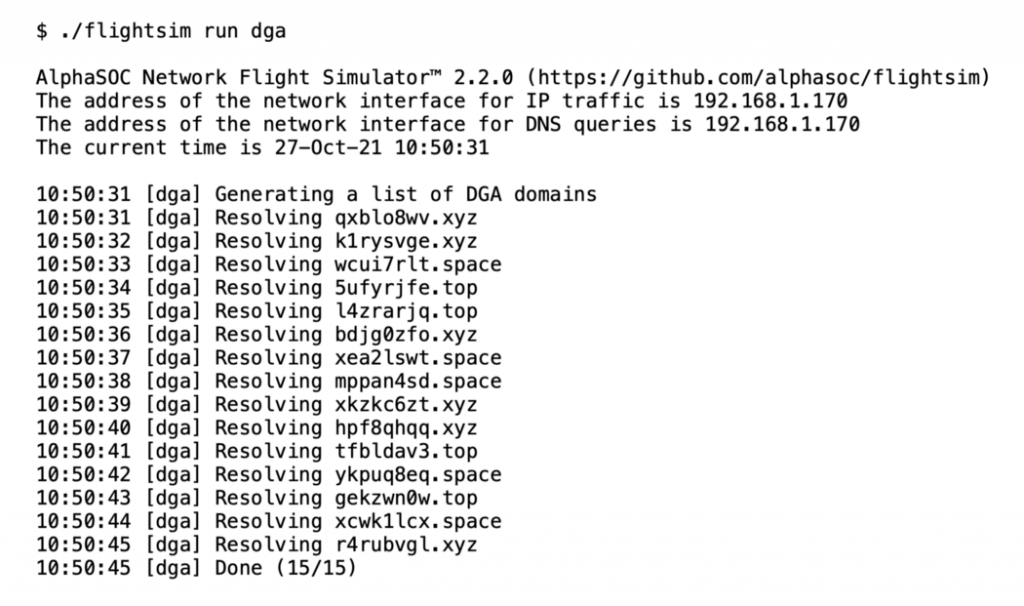
Domain Generation Algorithm (DGA) Traffic Simulation
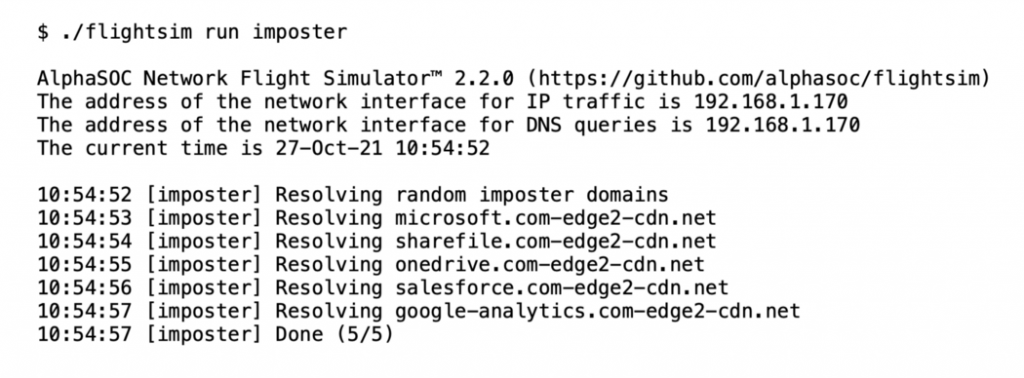
Simulating Traffic to Lookalike Imposter Domains
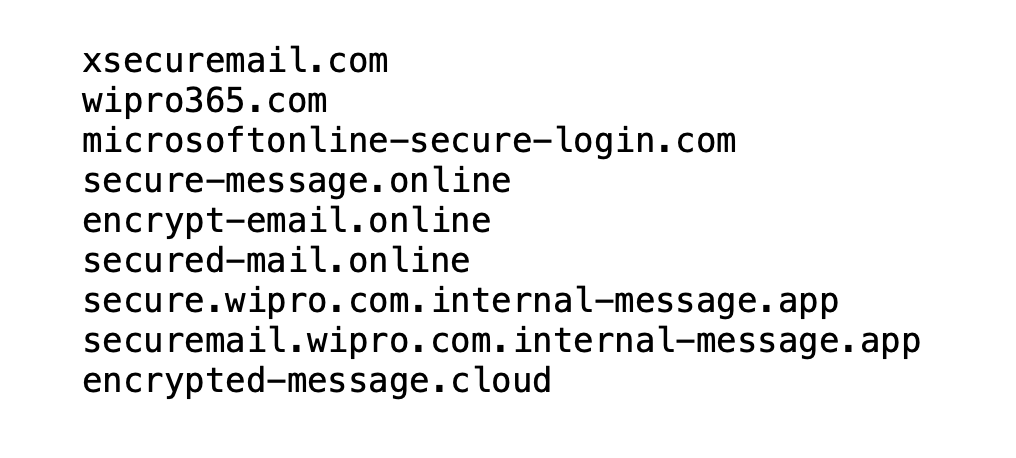
- Detecting traffic to lookalike imposter domains is critical within enterprise environments, as the threat actor who successfully compromised Wipro had used similar domains to evade detection, as listed here.
Within the AlphaSOC Analytics Engine we detect these lookalike domain patterns, along with many others, as discussed within previous blog posts:
- Moving Beyond Indicator Lists
- Automating the Hunt
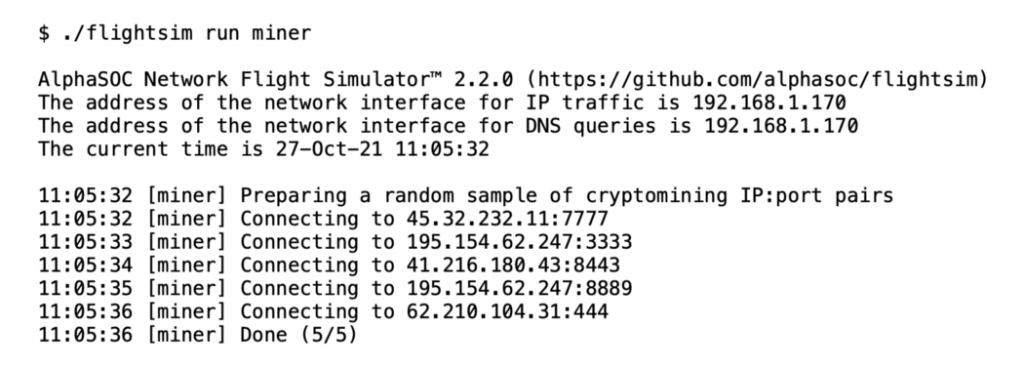
Cryptomining Simulation
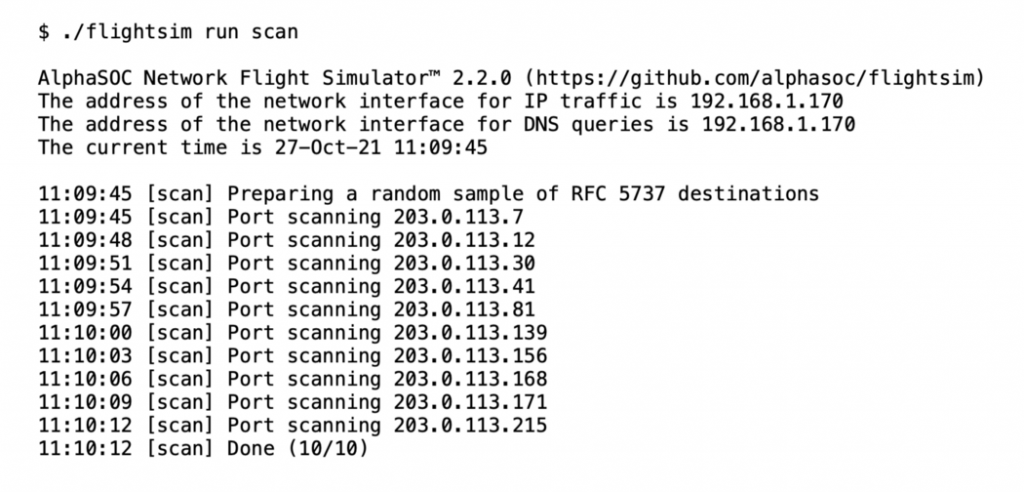
Outbound Port Scanning Simulation
Infected hosts commonly perform outbound network scanning, which we simulate within flightsim using the scan module. First we prepare a list of RFC 5737 destinations, and then generate TCP/IP traffic to common ports on each to simulate an outbound port scan, as below.
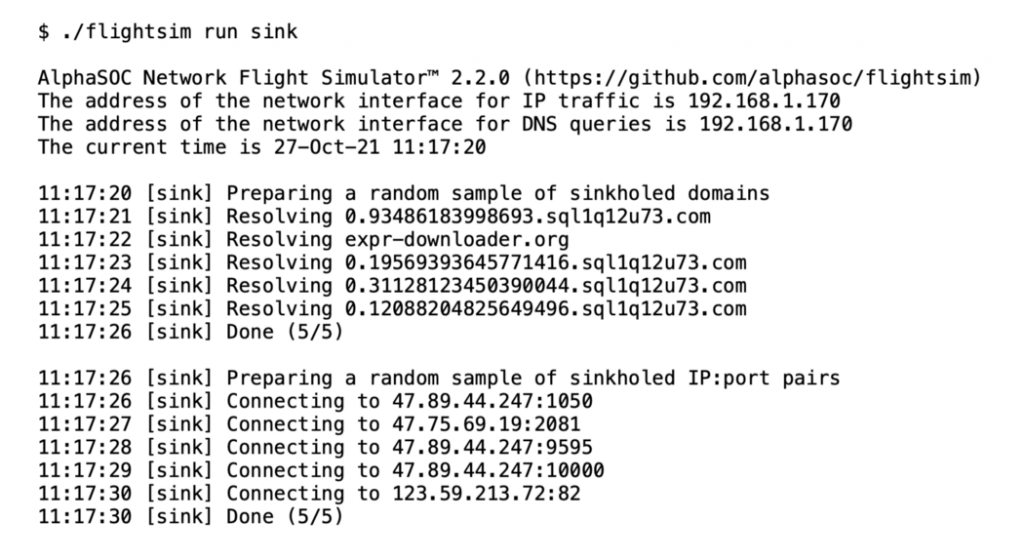
Sending Traffic to Known Malware Sinkholes
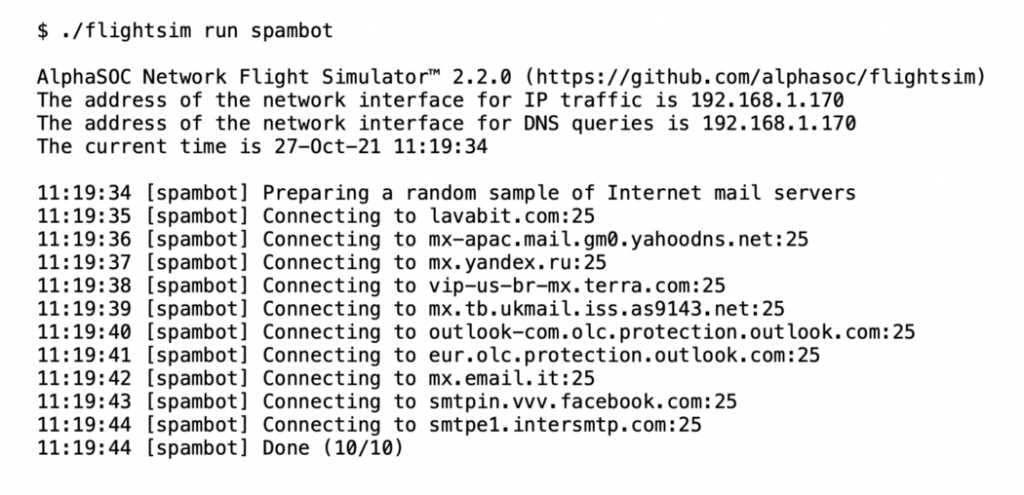
Connecting to Multiple SMTP Servers
Simulating SFTP / SSH Exfiltration
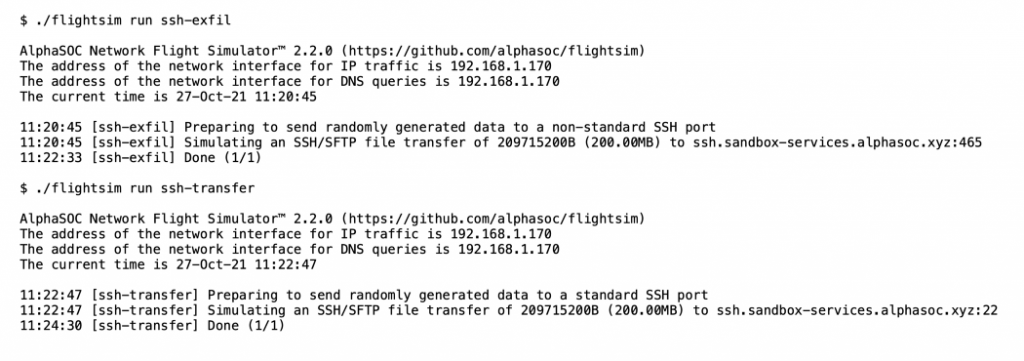
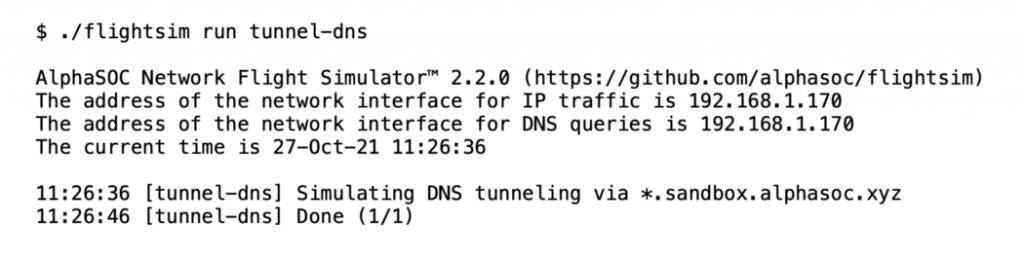
DNS Tunneling Simulation
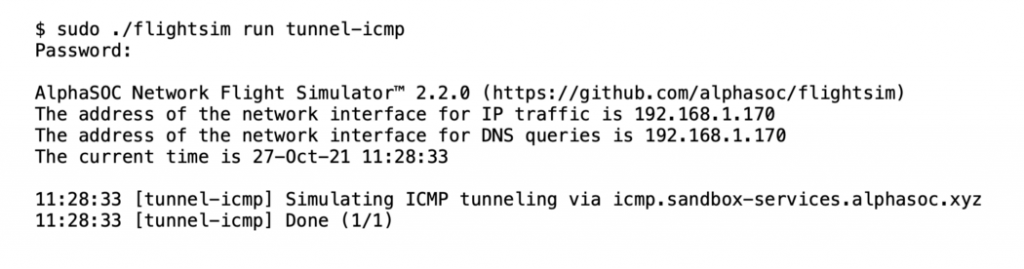
ICMP Tunneling Simulation
Improving Coverage and Visibility
Teams can operationalize Network Flight Simulator to generate malicious traffic patterns within their environments to ensure coverage of various C2 and exfiltration patterns, along with cryptomining, port scanning, spambot traffic, and spear phishing traffic to lookalike imposter domains.
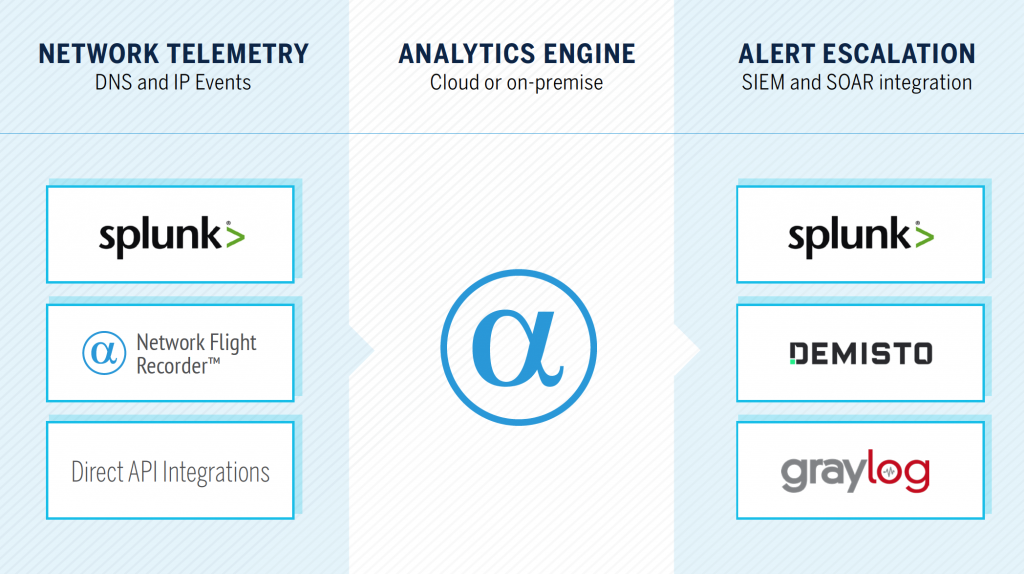
The AlphaSOC Analytics Engine supports detection of the patterns found within flightsim, and generates high fidelity alerts to support both reactive triage and proactive threat hunting activities, as summarized below.
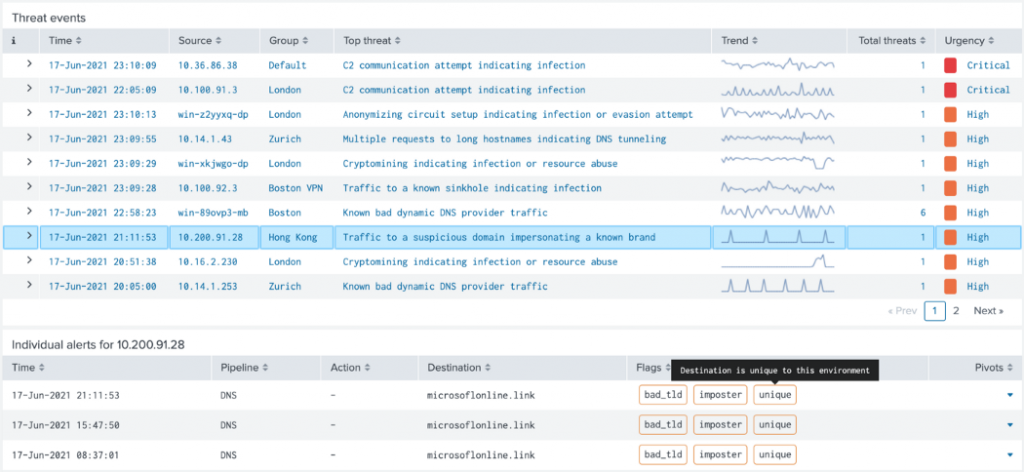
This screenshot is of our Network Behavior Analytics for Splunk integration. The AlphaSOC Analytics Engine can natively integrate with Splunk, Elastic, Snowflake, Amazon S3, and many other sources, and escalate alerts to any SIEM or SOAR platform, along with Slack, and other destinations.
Please get in touch for a demo, and to discuss your requirements further – sales@mintsecurity.fi.
AlphaSOC
Instantly identify infected hosts Uncover data exfiltration channels Threat hunt with high fidelity alerts Accurately identify security threats Hundreds of security teams around the world

Uncover Detection Blindspots with Network Flight Simulator
Today at AlphaSOC we released Network Flight Simulator (flightsim) 2.2.1, which is our free, open source adversary simulation tool. This latest release includes a number of new modules that security teams can use to instantly evaluate detection and response coverage within SIEM and SOAR tools.
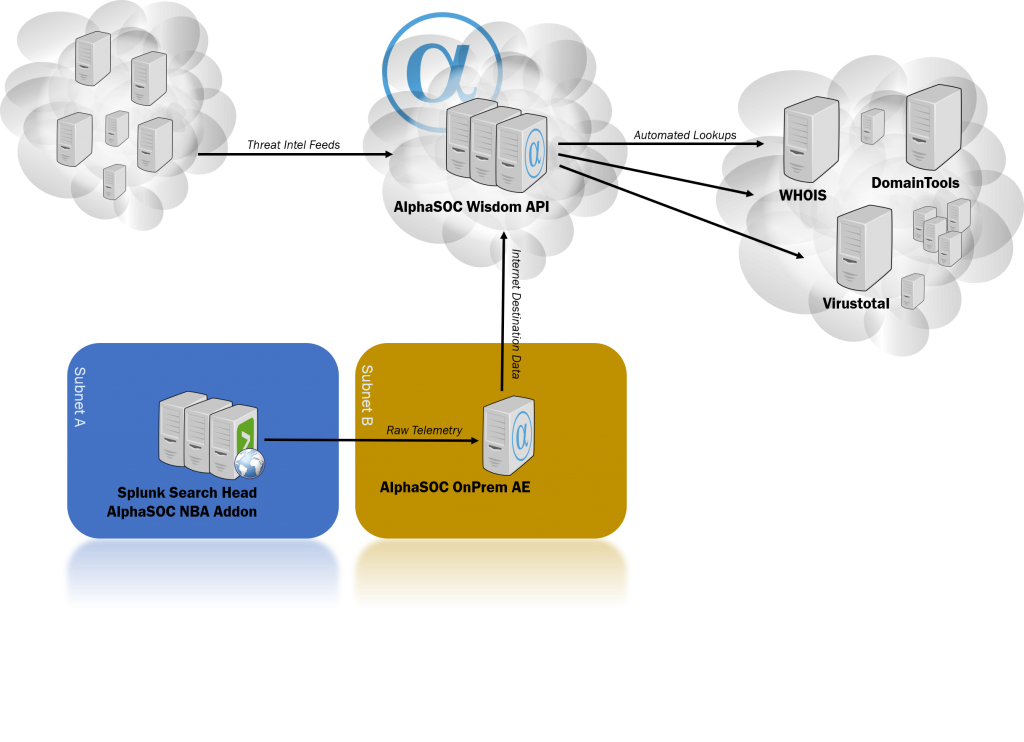
Different AlphaSOC deployment options
“The cloud!” somebody shouts out loud. “This means my data is sent to the cloud – my precious telemetry data that in the hands of the bad guys could reveal too much about myself!”. This is correct. And for the sake of transparency, let’s have a look at what actually goes on behind the scenes.

Mint Security to resell AlphaSOC solutions
Mint Security will start to resell and support the AlphaSOC product line in Finland and Europe.
Automating the Hunt
Through Network Behavior Analytics for Splunk and our native integrations for Demisto and Graylog, we instantly enrich network indicators (FQDNs, URLs, and IP addresses) to provide security teams with hunting material.