
- SAST - Static Application Security Testing
- SCA - Software Composition Analysis
- SDLC Integration
Manage Your Entire Application Security Program on a Single Platform

Veracode’s unified platform assesses and improves the security of applications from inception through production so that businesses can confidently innovate with the web and mobile applications they build, buy and assemble as well as the components they integrate into their environments.
Veracode offers a holistic, scalable way to manage security risk across your entire application portfolio. Veracode is the only solution that can provide visibility into application status across all testing types, including SAST, DAST, SCA, and manual penetration testing, in one centralized view,
Mint Security implements, complements and supplements
Mint Security integrates, coordinates and innovates your secure software development lifecycle. By adding Veracode tools to the mix, we deliver a holistic and elegant solution for both your development and management teams.
Contact us for a quick demo – even over Teams. We scan your code – for free – and show you real-life findings. After successfully showing actual value, we run a PoC where you can get your hands dirty. We can even do integrations during the PoC.
lines of code scanned
flaws fixed
in Gartner MQ for AST
customers globally
By Experts – For Experts

Veracode was founded by experts from leading application security companies to help organizations achieve code security more effectively and cost-efficiently. By delivering static analysis as a service, instead of an on-premises product, Veracode’s solution enables companies to forgo capital expenditure in vulnerability assessment software and hardware. Because Veracode is automated and easy to use, companies no longer need to hire security assessment experts or consultants. Because Veracode’s static analysis assesses compiled applications instead of source code – Veracode can test 100 percent of an application, offering comprehensive coverage and greater application security.
With its powerful combination of automation, process and speed, Veracode seamlessly integrates application security into the software lifecycle, effectively eliminating vulnerabilities during the lowest-cost point in the development/deployment chain, and blocking threats while in production. This comprehensive solution is managed through one centralized platform and stems from a powerful combination of best-in-class technology and top-notch security experts who offer remediation coaching and guidance on processes.
For developers
Veracode makes writing secure code just one more aspect of writing great code. With our designed-for-developer tools, API and workflow integrations, and tips for fixing vulnerabilities when they are found, you can make security a seamless part of your development lifecycle without sacrificing speed or innovation.
For Security Professionals
With Veracode, application security can meet the needs of developers while still satisfy reporting and assurance requirements for the business. Veracode’s ability to provide the right solutions for each stage of the software lifecycle ensures the applications that companies build and buy — and the third party components they use — are secure.
For Executives
Veracode delivers the application security solutions and services today’s software-driven world requires so that innovation and security can go hand-in-hand. Veracode customers ramp up quickly, see value on day one, demonstrate compliance with regulations, and easily scale over time.
For Operations
Veracode provides solutions that ensure the security of an application all the way through deployment. Operations teams can get better insight about attacks on production applications – and protect against compromise – without impacting performance. And when new vulnerabilities are discovered in open source components already in use they can quickly find and remediate those risks.
What is SAST?
Static analysis is one of the many code review tools that can be implemented without actually executing, or running, the software. Static analysis tools look at applications in a non-runtime environment. This method of testing has distinct advantages in that it can evaluate both web and non-web applications and, through advanced modeling, can detect flaws in the software’s inputs and outputs that cannot be seen through dynamic web scanning alone. In the past, this technique required source code, which is not only unpractical, as source code often is unavailable, but also insufficient. The Veracode static analysis service assesses binary code (also called “compiled” or “byte” code) instead of source code, which enables enterprises to test software more effectively and comprehensively, providing greater security for the organization.
More details
Patented technology
Unique in the industry, our patented binary static application security testing (SAST) technology analyzes all code — including third-party components and libraries — without requiring access to source code. SAST supplements threat modeling and code reviews performed by developers, finding coding errors and omissions more quickly and at lower cost via automation. Our technology is typically run in the early phases of the Software Development Lifecycle because it’s easier and less expensive to fix problems before going into production deployment.
The hunt for vulnerabilities
Our SAST technology identifies critical vulnerabilities such as SQL injection, cross-site scripting (XSS), buffer overflows, unhandled error conditions and potential back-doors. It classifies and prioritizes the vulnerabilities using standard NIST severity levels. Actionable information is delivered to help developers address them quickly, including detailed remediation information.
How Binary SAST Works
Binary SAST analyzes binary code to create a detailed model of the application’s data and control paths. The model is then searched for all paths through the application that represent a potential weakness. For example, if a data path through the application originates from an HTTP Request and flows through the application without validation or sanitization to reach a database query, then this would represent a SQL Injection flaw.
Binary SAST Delivers Deep Visibility
Our binary SAST technology makes it faster than ever to find and fix vulnerabilities in your applications. It delivers detailed information that: Is accurate: Static binary analysis examines applications the same way attackers look at them: By creating a detailed model of the application’s data and control flows. Unlike legacy source code scanners, this approach accurately detects hidden threats such as backdoors that are difficult to detect because they’re not visible in source code.
Into the deep end of things
Is actionable: Prioritized results can be accessed via standard bug tracking systems such as JIRA or Bugzilla or viewed through our web interface. Flaw details and remediation advice are automatically provided to aid in rapid mitigation or remediation. Minimizes false positives: Legacy scanning tools have a reputation for generating a high volume of vulnerabilities, which lowers productivity because of the time required to identify false positives. Our centralized platform is backed by world-class security experts and continuously learning with every new application it scans, to reduce false positives so you can start remediating faster.
What is SCA?
SCA means composition analysis – all your libraries. Veracode SCA protects your Java, Javascript, and .NET applications from open source risk by identifying known vulnerabilities in open source libraries used by your applications. In addition to providing a list of vulnerabilities when your application is scanned, Veracode SCA can also alert you when new vulnerabilities are discovered after your application has been scanned or when existing known vulnerabilities have had their severity level upgraded. Integrated with Jenkins for your build pipeline, you can fail your build based on vulnerabilities discovered as well as any components that your security team has blacklisted. As part of the Veracode Platform, Veracode SCA provides a unified experience to display all of your security testing results in one place. Additionally, the platform provides unified management of users, policies, mitigations, and integrations.
Highlights of SCA
- SCA uses a proprietary database of 3 million vulnerabilities which have been collated by machine learning. This means that we can find issues before they have been given CWE numbers and you are always first to know about new issues that are coming out
- SCA can provide dependency analysis and show vulnerabilities not only in the components that the customer software is using, but in the dependencies of those components.
- SCA uses something called vulnerable methods to show only vulnerabilities in the components the application is using, not just everything in the library, massively speeding up remediation time.
Reducing License Risk To Your Business
Many open source libraries have licenses that, when used in commercial purposes, can cost your organization millions of dollars. Veracode provides more than just vulnerability findings in our SCA product, we can also point out when your company is taking on license risk. Our SCA solution tells you which licenses you are exposing your application to, so you can take the proper steps to address them before going into production.
Standards and regulation
This is a nonexhaustive list of standards which require SCA to be in place.
- DORA (RTS)
- ISO 27001:2022
- IEC 81001-5-1
- ISA / IEC 62443-4-1
For more information, please refer to this blog https://www.mintsecurity.fi/en/3rd-party-library-management-sca-various-frameworks-and-requirements/
Best practices
Several industry regulations and security frameworks require that you find and patch known vulnerabilities in your applications, including PCI DSS, OWASP Top 10, FS-ISAC, NIST, and HITRUST.
It takes too much time to secure too little. The result: a dangerous backlog. Your unaddressed security findings represent a business risk and a brake on software velocity. Reduce mean time to remediate (MTTR) from months to minutes or seconds. Veracode Fix gives your developers precious time back, and fixes flaws faster. On average, Veracode Fix can address 74% of Java vulnerabilities discovered by Veracode SAST, without your developers writing a single line of new code.
See more about Fix here – https://www.veracode.com/fix
Responsible AI
Although open-source code provides a good training environment for fixing vulnerabilities, the potential for model poisoning is a serious risk. Veracode Fix is Responsible AI in Practice. Veracode Fix is NOT trained on open-source code, code in the wild, or customer data.
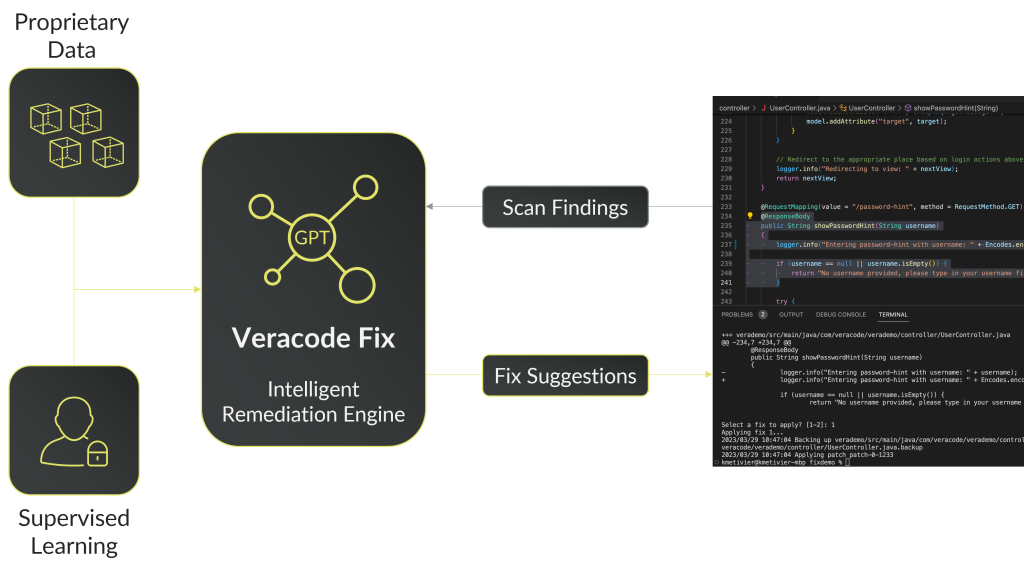
Veracode gives you the ability to scan your code and your libraries, right in your favorite IDE, while you are coding. You’ll receive positive feedback when you are correctly using secure coding practices, as well as instant insight into any security flaws that are discovered.
The majority of the scans done with Veracode IDE Scan complete in seconds (mileage may vary by programming language). This means you are getting feedback before you get too far, that’s the speed of SecDevOps. Veracode IDE Scan scans files, classes, or small packages and delivers those results back to your IDE in seconds. It’s a personal security coach while you code, pointing out security flaws right away so you can fix them immediately.
This isn’t just about your code, this is about you! Our aim with Veracode IDE Scan is to help developers around the world, such as yourself, build better and more secure code. Every day you are building the applications that are powering our entire world, and we want to make sure we are giving you the tools to be successful today and tomorrow.
- No “Scan & Scold” – fix your flaw before you even commit your code
- Better remediation advice with code examples
- Positive feedback when best practices are followed
- In line education, learning as you code
- Become a better developer – build your career around it
Supported platforms
Review the most up-to-date list of supported platforms here – https://docs.veracode.com/r/IDEs
We have all the integrations
Integrating has a twofold meaning – we integrate into your process and we integrate into your tools.
For a complete and up-to-date listing on all different aspects of integrating with the Veracode platform, always refer to https://docs.veracode.com/r/Veracode_Integrations
Troubleshooting
Contact us at support@mintsecurity.fi.
Please feel free to contact your Veracode representative as well. Your license contains support, make use of it.
Language support
https://docs.veracode.com/r/r_supported_table
Packaging support
Current hot topics
3rd party library management – SCA – various frameworks and requirements
Yhä useampi standardi, viitekehys ja asiakasvaatimus edellyttää – peräti huutaa – kirjastonhallinnan perään. Huutaa siksi että modernit sovelluskehitysmenetelmät ovat täysin riippuvaisia ulkoisista kirjastoista eli riippuvuuksista.

Veracode State of Software Security 12
Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
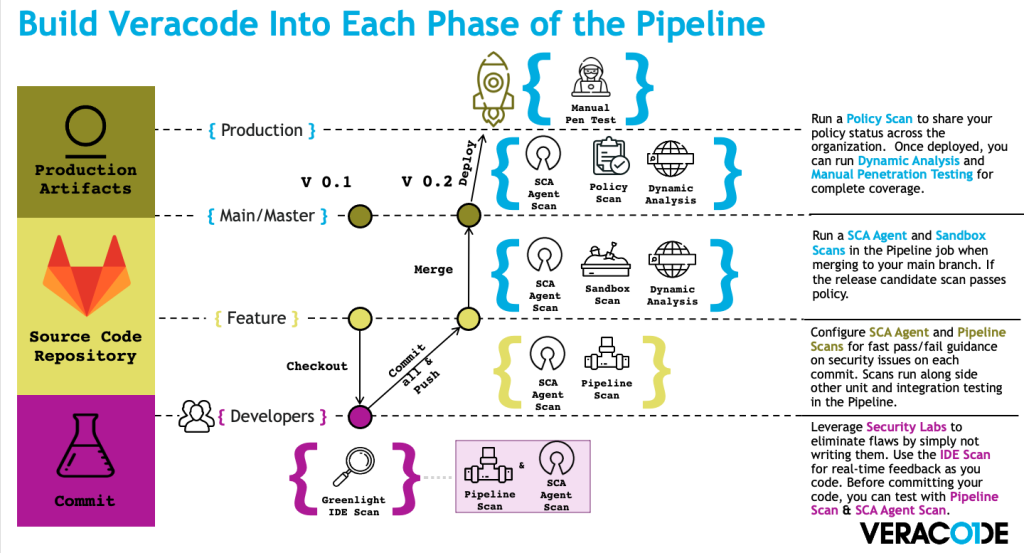
Hands-on Veracode guidelines for Azure, Gitlab and Github CI/CD pipelines
While docs.veracode.com (formerly known as help.veracode.com) is an excellent resource, it is not the most obviously intuitive tool out there. There’s got to be a

Veracode Webinar – Security scanning in pipelines
Julian (Veracode) and Thomas (Mint Security) show demos and presentations about running Veracode in CI/CD pipelines.

Veracode Security Labs Demo
22.09.2020 We at Mint Security wanted to have a look at… We scanned Koronavilkku – these are our findings 30.06.2020 Developers are, in effect, the

We scanned Koronavilkku – these are our findings
We at Mint Security wanted to have a look at the Koronavilkku application and pitch in. The application proved to be of very high quality securitywise. There were no significant security findings.
